How To Get HITRUST Certification: 10-Step Checklist
Last updated:22 October 2025

If you’re involved in security or compliance processes in a healthcare or tech company, you’ve probably heard this more than once: “Do we have HITRUST?”, usually followed by a mix of urgency and uncertainty.
Maybe a key client now requires it. Maybe you’re expanding into healthcare and need proof that your security meets industry expectations. Or maybe you’re already trying to comply with HIPAA, SOC 2, and ISO 27001 and wondering if HITRUST will finally help you unify it all or just add more work.
In 2024, a cyberattack on Change Healthcare disrupted claims processing nationwide. The company handles roughly 50% of U.S. medical claims, according to Reuters. The ripple effect was immediate: hospitals couldn’t get paid, patients faced billing delays, and insurers struggled to process reimbursements.
Incidents like this make one thing clear: security failures in healthcare don’t just affect data, but can destabilize the entire ecosystem. That’s the kind of systemic risk HITRUST was designed to mitigate.
HITRUST certification can seem complex at first. It’s highly structured, evidence-driven, and demands coordination across your entire organization. But it’s also one of the most credible ways to prove that your data protection program is both mature and trustworthy.
This article breaks down what HITRUST compliance actually means, who needs it most, and how to get HITRUST certified step by step.
Key Takeaways
- HITRUST certification validates that your organization’s security and privacy controls meet recognized industry best practices and standards.
- The HITRUST CSF unifies multiple existing frameworks, including HIPAA, NIST, ISO 27001, and GDPR, into one certifiable structure.
- Certification is independently assessed. This gives clients and regulators confidence that your controls are proven, not self-declared.
- HITRUST certification is increasingly required across healthcare, insurance, life sciences, and HealthTech, and strongly recommended for vendors handling PHI or PII.
- Core HITRUST compliance requirements include governance, risk management, access control, encryption, incident response, continuity planning, and vendor oversight.
- HITRUST framework uses a maturity model (PRISMA) that scores how well controls are designed, implemented, and continuously improved.
- Ongoing success depends on continuous monitoring and annual reviews.
- Working with experienced assessors and partners like TechMagic helps teams cope with MyCSF, remediation, and evidence collection efficiently.
What Is HITRUST Compliance?
HITRUST compliance means your organization meets the data protection standards defined by the HITRUST CSF, a security and privacy framework that brings together controls from HIPAA, ISO 27001, NIST, GDPR, and other major regulatory requirements.
In simple terms, it’s one unified framework that replaces the chaos of managing multiple overlapping ones.
The HITRUST CSF (Common Security Framework) was created to help organizations prove that their security and privacy programs are comprehensive and consistently enforced. It’s widely adopted and recognized across healthcare, insurance, and other regulated industries as the gold standard for verifying data protection maturity.
Unlike self-attested frameworks, HITRUST certification is independently validated by an external assessor and verified by the HITRUST Alliance. That means your security posture is based on real, tested evidence.
What's impressive, HITRUST reports a 99.41% breach-free rate among HITRUST certified environments. This vendor claim proves that the framework relies only on leading security practices, which are verifiable and evidence-based.
For most organizations, HITRUST certification is a strong signal of reliability and accountability. HITRUST assures customers and partners that your systems are protected by a mature, rigorously evaluated security compliance program.

Who Needs HITRUST Certification?
HITRUST certification is most relevant for organizations that handle sensitive health or personal data and need to prove they protect it according to industry-recognized standards.
In practice, it’s the go-to standard for companies working with protected health information (PHI), personally identifiable information (PII), or regulated financial data and for any vendor that supports those environments.
Let’s look at the sectors where HITRUST is now expected.
HealthTech and healthcare organizations
Hospitals, clinics, and digital health platforms process massive amounts of PHI daily. HITRUST certification helps them demonstrate compliance with HIPAA requirements and other privacy laws. This assures patients and partners that security controls are actively monitored and validated.
For teams still dealing with the foundational steps, our HIPAA compliance checklist provides a clear breakdown of essential administrative, physical, and technical safeguards every healthcare organization should implement.
Pharmaceutical and life sciences companies
Drug manufacturers, clinical research organizations, and biotech startups rely on secure data sharing for trials, research, and patient management. HITRUST ensures that data handling, consent tracking, and third-party collaboration meet the same high security standards as healthcare delivery systems.
Health insurance and payer organizations
Payers and insurers manage sensitive member records, claims, and payment data across multiple systems. HITRUST certification provides an efficient way to show alignment with Health Insurance Portability and Accountability Act and CMS requirements and reduces the complexity of third-party audits.
Business associates and third-party vendors
Any company that stores, processes, or transmits PHI or PII on behalf of another organization, such as billing services, analytics platforms, or IT providers, often needs HITRUST certification to maintain or win healthcare contracts.
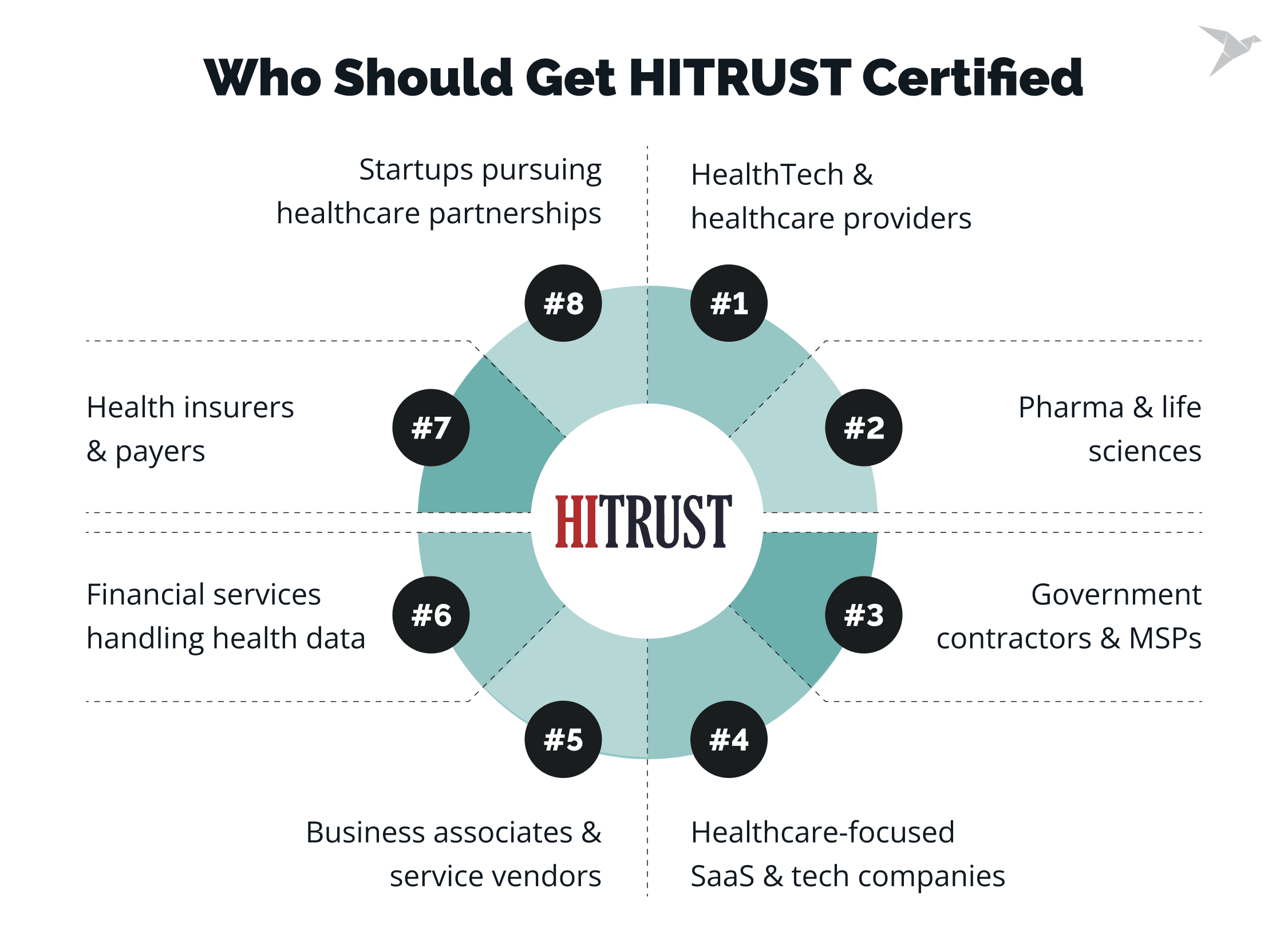
Technology and SaaS providers serving healthcare
EHR vendors, telehealth apps, and AI-based healthcare tools frequently integrate with hospital or insurance systems. HITRUST certification gives these companies a competitive advantage as it proves that their infrastructure and processes are compliant and protected.
Financial services and insurance technology firms
Payment processors, benefits administrators, and fintechs handling health-related transactions fall under overlapping compliance obligations. HITRUST helps unify HIPAA, PCI DSS, and SOC 2 compliance requirements into one validated framework and simplifies their risk posture.
Government contractors and managed service providers (MSPs)
Organizations that support government or state health programs, such as Medicaid systems, public sector IT vendors, or hosting providers, are increasingly requested to demonstrate HITRUST alignment to meet NIST 800-53 security expectations.
Growing startups seeking healthcare partnerships
New HealthTech startups often pursue HITRUST early to accelerate trust with hospitals, insurers, and investors. Certification shortens procurement cycles and signals that their security and privacy practices are mature enough for enterprise-grade partnerships.
What Are Key HITRUST Requirements?
To achieve HITRUST certification, your company must demonstrate control effectiveness across multiple domains, including governance, information risk management, technical safeguards, vendor oversight, and continuous monitoring.
Each of HITRUST requirements maps to standards like NIST 800-53, ISO 27001, and HIPAA Security and Privacy Rules. This ensures your program aligns with recognized global frameworks.
Here are the key HITRUST certification requirements in detail.
Information security management and governance
Organizations need a documented governance model defining who owns, implements, and enforces security policies. Leadership must oversee a formal ISMS (Information Security Management System), supported by governance committees, periodic policy reviews, and executive accountability. HITRUST assessors look for clear evidence that information security is embedded in decision-making, not treated as an isolated function.
Risk management and assessment
HITRUST requires a repeatable risk management process: identifying threats, assessing likelihood and impact, and prioritizing mitigation. You must document risk registers, assign owners, and regularly re-evaluate risks as your environment or business model changes. Risk treatment plans should map directly to CSF control objectives and show measurable outcomes.
Access control and identity management
Access to systems containing regulated data must follow the principle of least privilege. Organizations must implement strong authentication (like MFA), enforce role-based access, maintain provisioning/deprovisioning workflows, and review access logs at defined intervals. The HITRUST approach expects documented IAM policies and proof of enforcement in production systems.
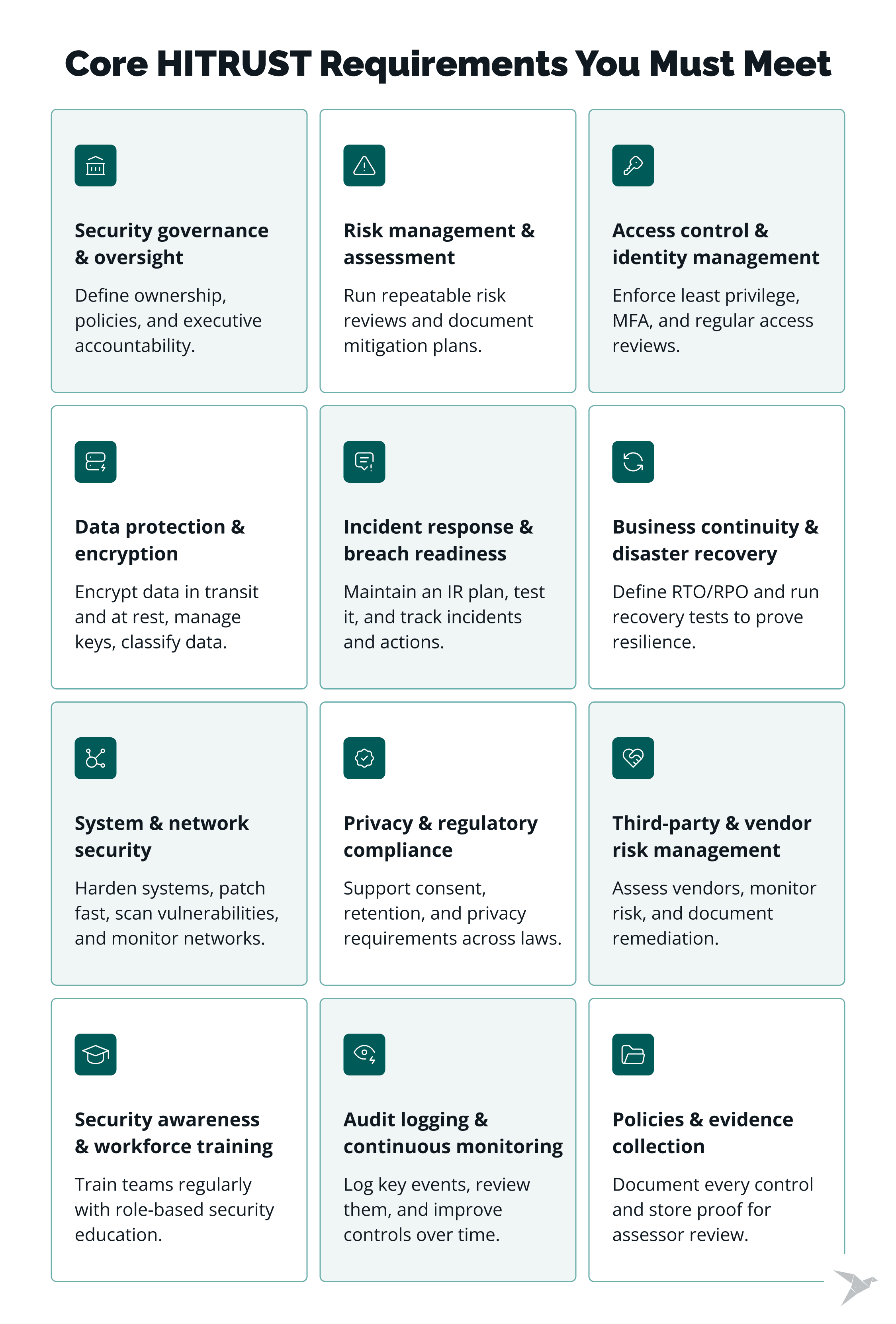
Data protection and encryption standards
Sensitive information must be encrypted both at rest and in transit using algorithms that meet current industry standards (such as AES-256 and TLS 1.2+). Controls should also cover key management procedures, data classification, and secure disposal of media. HITRUST assessors verify that encryption and data handling policies are consistently applied across endpoints, cloud services, and backups.
Incident response and data breach management
A formal incident response (IR) plan must define detection, escalation, containment, and recovery steps. The plan should identify key roles, communication channels, and notification requirements under HIPAA compliance and other laws. Regular tabletop exercises or simulations are required to test readiness. Assessors review IR logs, training records, and after-action reports for completeness.
Business continuity and disaster recovery planning
Organizations must maintain operational resilience through tested business continuity and disaster recovery plans. These include identifying critical assets, defining RTO/RPO metrics, and performing at least annual recovery tests. Documentation must show how essential functions are maintained during outages and how restoration meets defined timelines.
Third-party and vendor risk management
Any vendor or contractor with access to PHI, PII, or production systems must undergo due diligence and continuous monitoring. This involves tiering using risk-based approach, signed security agreements, periodic reassessments, and incident reporting expectations. HITRUST assessors look for evidence of vendor inventories, risk scoring, and remediation follow-ups.
Privacy and regulatory compliance controls
HITRUST integrates privacy-by-design principles. You must have policies covering lawful data collection, consent management, and retention schedules aligned with state regulations like HIPAA, GDPR, and CCPA. Organizations are expected to maintain records of processing activities and demonstrate controls for limiting access, anonymizing data, and responding to data subject requests.
System and network security controls
This domain focuses on technical hardening and defense. Controls include secure configuration baselines, vulnerability scanning, timely patch management, and continuous network monitoring. Firewalls, IDS/IPS, endpoint protection, and segmentation should be deployed and regularly tested. HITRUST assessors evaluate logs, patch reports, and vulnerability management workflows.
Security awareness and workforce training
A comprehensive security training program ensures employees understand their security responsibilities. Training must cover phishing awareness, acceptable use, data handling, and incident reporting procedures. Role-based training is required for administrators, developers, and support staff. HITRUST expects documented completion rates and evidence of ongoing education.

Audit logging, monitoring, and continuous improvement
Security events must be logged, correlated, and reviewed regularly. Logs should capture authentication attempts, configuration changes, and privileged activity across systems. Organizations are also expected to perform periodic internal audits and control reviews. Continuous improvement (through metrics, lessons learned, and CAPs) is essential for maintaining certification readiness.
Policy documentation and evidence collection
Every implemented control must be supported by policy documentation and verifiable evidence. Examples include system configurations, screenshots, audit results, or training records. The HITRUST MyCSF portal is used to store and organize this evidence for assessor review, which ensures traceability and consistency across all control domains.
HITRUST Compliance Checklist
The HITRUST certification process follows a defined path: scope your environment, choose the right assessment, close gaps, prove control maturity with evidence, pass an external validation, and maintain it year over year. Here’s the sequence that works in practice.
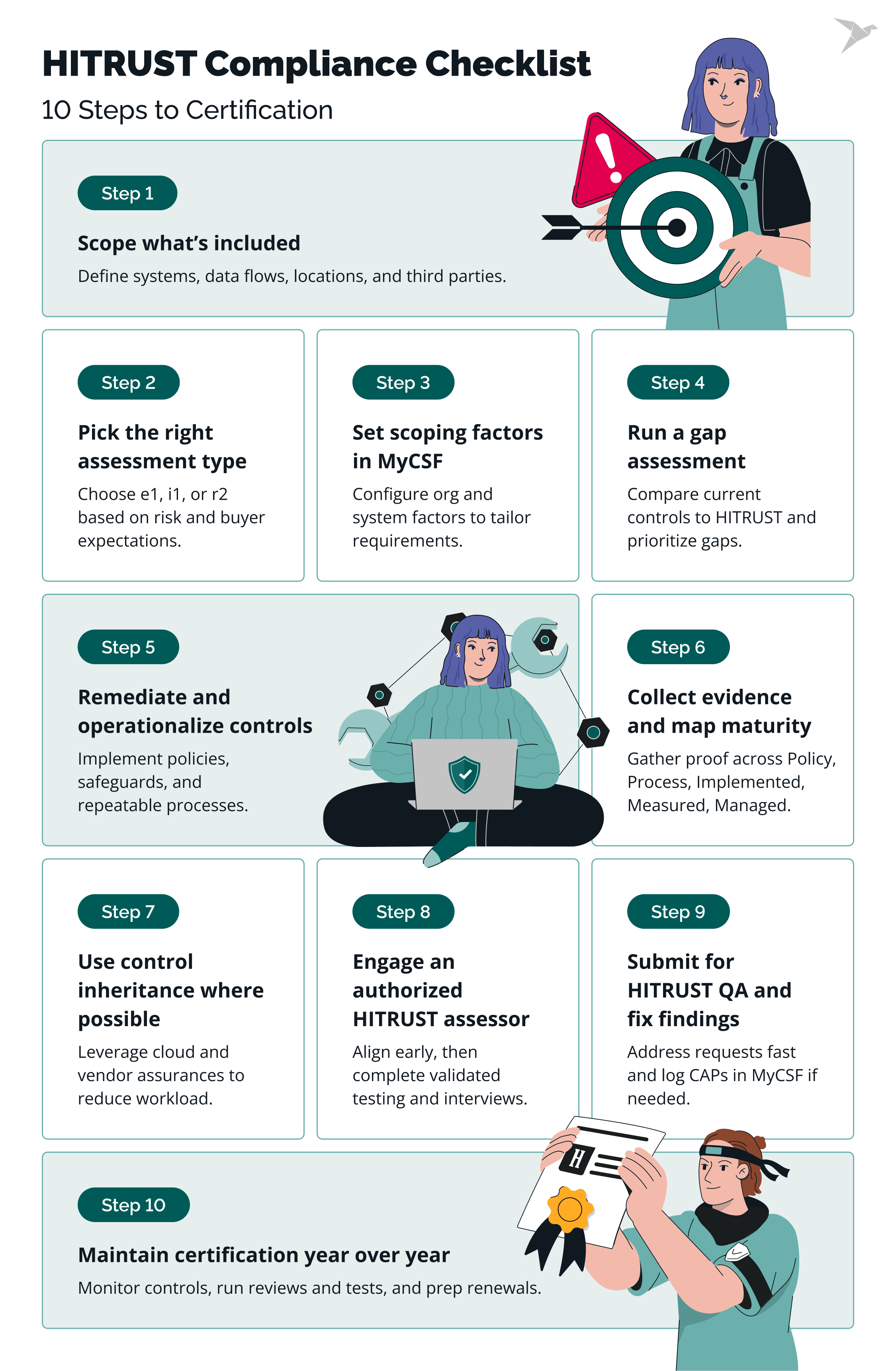
Step 1. Define scope and boundaries
Decide exactly what’s “in.” Identify systems, apps, data flows, and business units that store, process, or transmit PHI/PII. Map third parties and cloud service providers. Document data types, environments (prod/non-prod), and locations. Good scoping prevents wasted effort and missed controls.
Step 2. Choose the assessment type (e1, i1, or r2)
Match assurance level to risk profile and stakeholder expectations:
- e1 assessment (essentials): baseline hygiene; fastest, lowest assurance.
- i1 assessment (implemented): strong baseline with evidence of implementation; 1-year validity.
- r2 assessment (risk-based validated): highest assurance, full control maturity scoring (Policy/Process/Implemented/Measured/Managed), 2-year validity with an interim assessment review.
If you sell into large healthcare enterprises or handle sensitive PHI at scale, expect r2 to be requested.
Step 3. Set scoping factors in MyCSF
Configure organizational, regulatory, system, and implementation factors in MyCSF (such as data volumes, interfaces, hosting model, geography, and regulatory drivers). This tailors which requirement statements apply and to what extent.
Step 4. Run a readiness/gap assessment
Compare current controls to HITRUST CSF certification requirements. Produce a gap register: what’s missing, what’s partial, what lacks proof. Prioritize by risk and dependency (for example, IAM before app changes). This is where timelines and budget become real.
Step 5. Remediate and operationalize controls
Close the gaps with a focus on durability:
- Update and approve policies/standards.
- Implement technical safeguards (MFA, encryption at rest/in transit, logging, hardening baselines).
- Stand up repeatable processes (access reviews, vendor due diligence, patch SLAs).
- Prove they run: tickets, change logs, training records, scan results, playbooks, tabletop reports.
Step 6. Collect evidence and map to PRISMA
For each requirement, gather verifiable evidence that shows maturity across Policy, Process, Implemented, Measured, Managed. Use screenshots with timestamps, config exports, SIEM queries, vulnerability reports, DR test results, and meeting minutes. Ensure traceability: requirement → control owner → artifact → date.
Step 7. Leverage inheritance (cloud and key vendors)
Reduce scope where appropriate by inheriting controls from cloud providers and critical vendors that publish HITRUST-eligible assurances. Validate boundaries: what you inherit vs. what you still must implement (for example, your IAM, key management choices, app configs).
Step 8. Engage a HITRUST authorized external assessor
Select an assessor early, align on scope and timeline, and run a pre-validation check. During the validated assessment, expect interviews, sampling, control walkthroughs, and deeper testing around high-risk areas (access, encryption, incident response, DR, vendor risk).
Step 9. Submit for HITRUST QA and address findings
Your assessor finalizes scoring and submits to HITRUST for Quality Assurance. Be ready to clarify evidence or provide additional artifacts quickly. If any requirements fall short, document Corrective Action Plans (CAPs) with accountable owners and due dates in MyCSF.
Step 10. Maintain certification and prove ongoing performance
Once becoming HITRUST certified, keep it alive:
- Run continuous monitoring (logging, alerting, KPIs).
- Perform periodic access reviews, patch cycles, vendor reassessments, and IR/DR tests.
- Track CAP progress to closure.
- Prepare for the interim (year-1) review for r2 and full recertification at renewal.
Treat HITRUST as an operating rhythm, not a once-a-year scramble.
Partner with Experts Who Understand the HITRUST Journey
By the time most teams start their HITRUST journey, they’re already deep in compliance fatigue. Documentation feels endless, auditors keep changing expectations, and internal teams are stretched between maintaining security operations and proving them. That’s where you need the right partner.
At TechMagic, we help healthcare and tech organizations simplify every stage of the HITRUST certification process. Our security engineers, compliance consultants, and DevSecOps specialists work directly with your internal teams to comply with all HITRUST certification requirements effectively.
If you’re building your first HITRUST-ready environment or preparing for recertification, we’ll help you design a process that’s efficient, sustainable, and aligned with your broader security strategy.
If you’re ready to reduce compliance overhead and move confidently toward HITRUST certification, our team is here to help you get there faster with the same precision and care we apply to every security engagement.

Wrapping Up: The Future of HITRUST and Compliance Maturity
The HITRUST certification process isn’t quick. However, it's one of the clearest ways to prove your security program holds up under real scrutiny. It validates that your policies, controls, and daily operations protect sensitive data effectively.
For healthcare and technology companies, the payoff is solid: stronger client trust, fewer overlapping audits, and smoother vendor relationships.
The process demands structure, coordination, and detailed evidence. But once complete, it becomes a foundation your organization can build on year after year. With the right approach and expert support, your HITRUST certification process becomes a natural extension of security maturity.
Looking ahead, HITRUST is expected to play an even larger role in shaping unified compliance strategies. As healthcare data ecosystems become more interconnected and cloud-dependent, frameworks like HITRUST will continue evolving toward continuous monitoring, zero-trust architecture, and more dynamic assurance models.
Organizations that begin strengthening these capabilities today will be better prepared to adapt to new regulatory frameworks, reduce audit complexity, and maintain trust.
FAQ

What is HITRUST certification?
HITRUST certification is a formal validation that your organization meets the security and privacy requirements of the HITRUST CSF (Common Security Framework). It confirms that your controls are properly designed, implemented, and tested by an authorized external assessor.
Is HITRUST only for the healthcare industry?
No. HITRUST originated in the healthcare sector but is now used across multiple industries that handle sensitive or regulated data, including finance, insurance, SaaS, and government contractors.
What does HITRUST stand for?
HITRUST stands for Health Information Trust Alliance, the organization that developed and maintains the HITRUST CSF framework and certification process.
How much does HITRUST cost?
Costs vary widely based on scope, system size, and chosen HITRUST assessment and certification type. Smaller organizations might spend around $50,000-$100,000, while large enterprises can exceed $250,000, including third-party assessor fees, MyCSF licensing, and internal remediation work.
What is HITRUST certified?
An organization, system, or product is HITRUST CSF certified when it has passed an independent assessment and proved its security and privacy controls meet the HITRUST CSF standards.
Is HITRUST a cybersecurity framework?
Yes. The HITRUST CSF is a certifiable cybersecurity and compliance framework that integrates requirements from standards like NIST, ISO 27001, HIPAA, and GDPR into a single, unified control set.

 Software Development
Software Development Security Services
Security Services Cloud Services
Cloud Services Other Services
Other Services















 TechMagic Academy
TechMagic Academy