Security Risks of Artificial Intelligence: Examples and Ways of Defense
· 11 min read
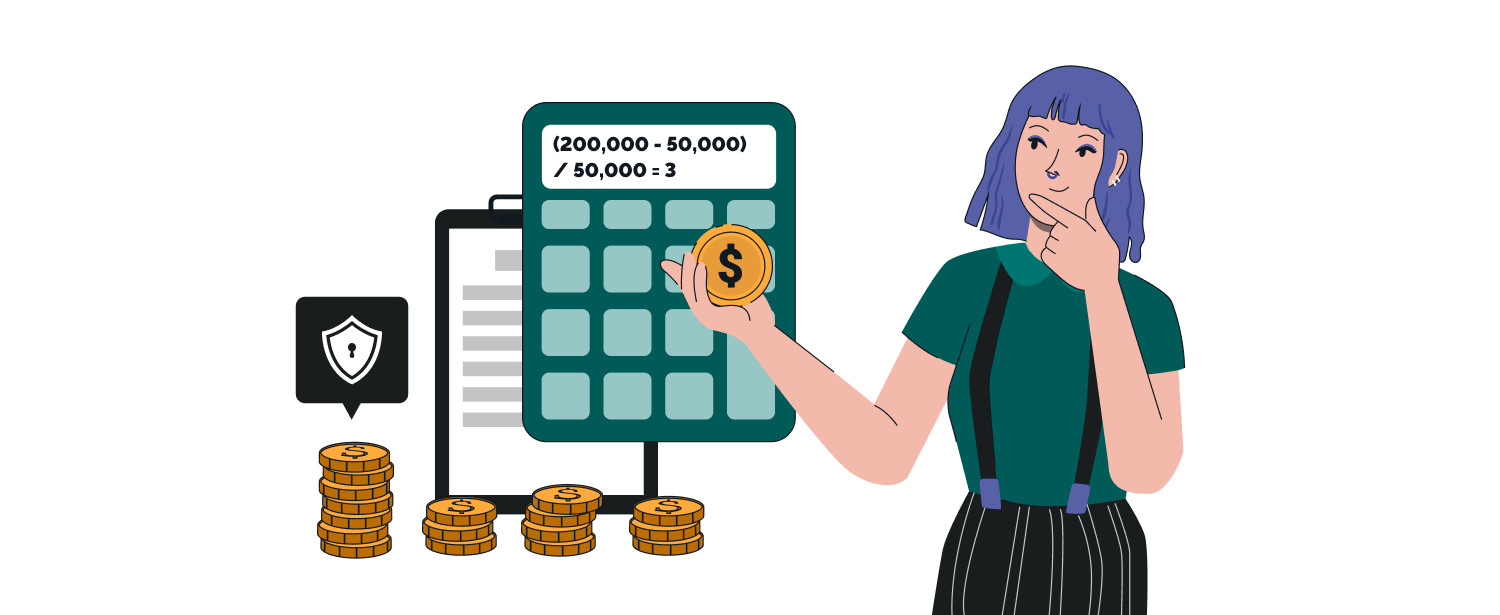
Artificial Intelligence is a truly mixed blessing. While it offers incredible advancements, one of its most unfortunate aspects is becoming a powerful weapon in the hands of bad actors. In most cases, AI security risks include data theft and disruptions to critical digital operations.

 Software Development
Software Development
 Security Services
Security Services
 Cloud Services
Cloud Services
 Other Services
Other Services
















 TechMagic Academy
TechMagic Academy