How To Hire a vCISO: A Step-by-Step Guide for Businesses Seeking Cybersecurity Leadership
Last updated:19 September 2025

As a leader with significant responsibility, you’re probably facing real friction every week: long security questionnaires from prospects, redlines on DPAs and data residency, buyers pushing for SOC 2 or ISO 27001 on tight timelines, and stakeholders demanding clean, board-ready risk reports…
Additionally, regulatory requirements continue to tighten. SEC incident disclosure in four business days, NIS2 widening scope, and DORA applying across EU financial services. The bar keeps rising steadily.
Inside the company, the security challenges are equally complex: unclassified data with inconsistent handling procedures, fragmented risk management without continuous monitoring, MFA bypass vulnerabilities in service accounts, configuration drift in cloud environments, unvalidated third-party security postures, untested incident response procedures, and tool sprawl without clear ownership or integration.
The numbers reinforce the urgency. IBM's 2025 data breach report puts the global average breach cost at $4.44M. Meanwhile, ISC2 estimates approximately 4.8M cybersecurity workforce gap.

Still, your fast-growing company may not be ready for a full-time CISO who'd handle everything on that list.
Therefore, a vCISO can be a practical, cost-effective solution for establishing security leadership. However, this model requires careful implementation to maintain security effectiveness. You'll need to ensure experienced security leadership that not only sets direction and governs risk, but also maintains continuous security oversight and incident response readiness without the investment of a full-time executive.
At TechMagic, we've seen these problems firsthand, helping fast-growing companies secure their operations with our vCISO services. We'll gladly share our security best practices to help you make a confident decision.
This article will help you understand how to hire vCISO for your stage and goals. We'll explain what a vCISO actually does, walk through a 12-step hiring guide, and flag common mistakes.
Key Takeaways
- Security leadership is scarce and expensive, but the vCISO model delivers senior expertise on a flexible, cost-effective basis. So it's a great solution for companies having resource constraints.
- ]True resilience does not equal perfection. True resilience is in faster detection, response, and recovery, which a vCISO drives.
- A vCISO translates technical risks into business terms and gives boards clear, decision-ready insights.
- vCISOs break down silos: they align cloud, vendors, compliance, and product teams under one security plan.
- Vendor and supply chain attacks are growing, and vCISOs bring proven oversight playbooks to manage that risk.
- With AI everywhere, a vCISO sets practical policies that let teams innovate without creating blind spots.
- Security metrics must measure actual security effectiveness: mean time to detect, containment effectiveness, and validated recovery capabilities.
- At TechMagic, we provide virtual CISO services with clear accountability structures, defined incident response authority, and continuous security monitoring integration.
Why Is There a Shortage of Cybersecurity Leadership Today?
In a nutshell, the risk keeps climbing faster than hiring can keep up. To be more specific, here are the main reasons explained:
Threats keep accelerating faster than teams can adapt
Attackers have evolved beyond simple intrusions. Ransomware and extortion now account for approximately 32% of breaches, while human error and misconfiguration remain significant attack vectors, according to Verizon. Teams must simultaneously manage daily security operations while maintaining business continuity and supporting growth initiatives. This leaves insufficient capacity for developing a comprehensive security strategy.
Regulation raised the bar everywhere
Governments now expect much faster and more detailed reporting. Public companies in the U.S. must disclose material cyber incidents within four business days (after determining materiality). In the EU, NIS2 expands the number of sectors in scope, and DORA is now applicable across financial services with strict ICT risk, testing, and third-party oversight. Even private companies feel the knock-on effect, as partners and investors expect higher compliance requirements.
Buyers demand proof, not promises
Security due diligence went from “a few questions” to standardized assessments. The Shared Assessments SIG Core runs 600+ questions across 21 risk areas, and many enterprises layer their own checks on top. Organizations must demonstrate not just documentation, but continuous monitoring, incident response capabilities, and third-party risk management. That's a challenging task without executive security leadership.

The talent gap is wide and growing
The global cybersecurity workforce gap reached approximately 4.8 million in 2024, up 19% year over year, according to ISC2. Teams report both staffing shortages and diverse skills gaps, especially in cloud, incident response, and AI security. Leadership positions are often the hardest to fill.
Third-party and software supply chain risk expands the remit
Verizon notes third-party software breaches at 15% of cases and a surge in vulnerability exploitation. Modern security leaders must govern vendors, SaaS, and partners, not just the internal network. That makes the leadership role broader and more complex than before.
Budgets and timing don’t line up with the need
Boards face increasing pressure, but hiring a skilled in-house CISO is slow and expensive. Many teams divert spending to services and managed capabilities while they search. This leaves a leadership gap right when questionnaires, audits, and incidents arrive.
To understand the solution, we first need to define the role: what is a vCISO? Let’s find the answer in the next section.
What Is a vCISO and How Does the vCISO Model Work?
Your organization may not yet require a full-time CISO. However, you still need someone accountable for comprehensive risk management, compliance oversight, and security strategy. Someone with demonstrated technical expertise and security leadership experience.
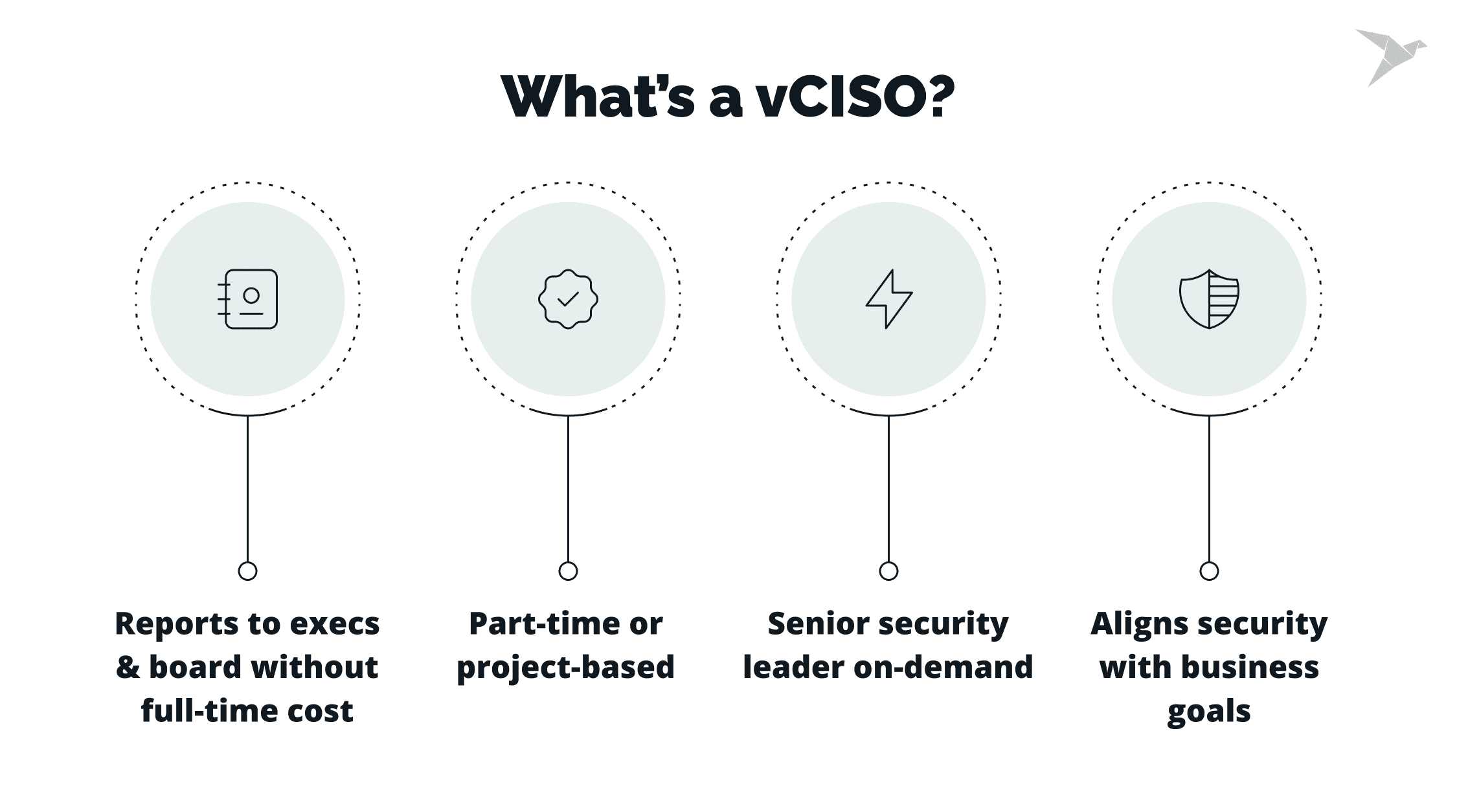
The best alternative is a virtual CISO (vCISO), an experienced security leader who sets direction, governs risk, and drives the security strategy forward.A vCISO is a senior security executive you engage part-time or for a defined project. vCISOs align security with business goals, make decisions, and report to leadership and the board without the cost and lead time of a permanent hire.

How an effective vCISO model should work
A vCISO engagement helps move fast and stay practical.
It usually starts with a short discovery phase (sometimes called gap assessment) to map business risks, existing security controls, and near-term priorities. After that, it shifts into a steady rhythm:
- Governance touchpoints with executives
- Working sessions with IT, engineering, and compliance
- Surge support when audits or incidents hit

You can shape the model to fit your stage:
- Fractional. A few days a month to steer strategy and keep alignment.
- Retainer. Ongoing leadership for vendor oversight, audits, and governance.
- Project-based. Tight, goal-driven engagements like SOC 2 readiness, ISO 27001, or incident recovery.
Decision rights stay clear. The vCISO sets direction, approves policies and exceptions, and manages risks. Day-to-day tasks (like hardening cloud configs, updating identity systems, or rolling out endpoints) stay with your internal security team or MSSP.
The point is to lead and enable, not replace.
Success is measured in business outcomes, not just security jargon. Typical metrics include:
- Risk reduction over time
- Audit readiness by control domain
- Time to remediate critical issues (MTTR)
- Incident response performance
- Impact on sales velocity when security reviews land
Here are vCISO engagement models in a quick-reference format:
If you're still weighing the differences between vCISO and CISO, we've broken it down in our vCISO vs CISO guide to help you make the right decision.
If the vCISO option is for you, we'll gladly explain how to find and hire vCISO wisely in the next section!
How to Hire a vCISO: Step-by-Step Process for Businesses [Guide]
Your goal is measurable security improvement, not just strategic advice. Use this guide on how to find virtual CISO to choose confidently and get measurable outcomes.
Step 1: Define business drivers, risk appetite, and objectives
Start with why. Tie security to revenue, compliance, and uptime.
Clarify priorities: closing enterprise deals, preparing for SOC 2/ISO 27001/HIPAA, or cutting incident risk. Align with the CEO and board on risk appetite: what you’ll accept, mitigate, transfer, or avoid.
Set 3-5 concrete objectives (like “SOC 2 audit in Q4,” “reduce critical findings by 60%,” “cut MTTR to <24 hours”).
Deliverable: one-page brief with security priorities, risk appetite, and success outcomes.
Step 2: Assess current security maturity and identify gaps
Get a quick, honest read on where you are today.
Review policies, cloud security posture, identity, third-party risk, incident readiness, and evidence for audits. Map controls to a familiar security framework (ISO 27001 or SOC 2) to keep the conversation consistent. Keep it lightweight, guide based on asset value, and focus on what blocks sales or raises real risk.
Deliverable: a short gap summary + a prioritized issues list (critical, high, medium).
Step 3: Outline scope of work, responsibilities, and success metrics
Convert findings into scope. Decide what the vCISO owns (governance, risk, audit readiness, IR oversight) and what stays with IT/engineering/MSSP. Write down decision rights, meeting cadence, and the artifacts you expect (risk register, roadmap, policy set, board updates).
Define measurable metrics: % control coverage, time to remediate criticals, audit milestones, deal velocity on security reviews.
Deliverable: a scope and outcomes document with clear KPIs/OKRs.
Step 4: Decide on engagement model and budget
Pick what fits your stage and deadlines:
- Fractional for ongoing direction
- Retainer for continuous governance and vendor oversight
- Project for a defined outcome (SOC 2, ISO 27001, HIPAA, incident recovery)
Align the model with your timeline and budget constraints. Plan for a modest surge during audits or incidents.
If SOC 2 readiness is on your roadmap, our SOC 2 consulting services can help you prepare efficiently and avoid delays.
Deliverable: an approved model (fractional/retainer/project), monthly budget, and term.

Step 5: Draft a role profile and statement of work (SOW)
Write a role profile that a senior exec would respect. Focus on outcomes. Be specific. In the SOW, spell out scope, deliverables, meeting cadence, reporting, decision rights, SLAs, data handling, and exit criteria. Keep it crisp to avoid ambiguity later.
For companies targeting ISO 27001 certification, our ISO 27001 consulting services provide tailored guidance and evidence-ready deliverables.
Deliverable: role profile + SOW ready to share with candidates/providers.
Step 6: Source candidates through trusted networks and providers
Use referrals from investors, portfolio peers, founders’ groups, and your audit firm. Check credible marketplaces or service partners who can stand behind delivery. Ask for relevant case studies: similar size, similar industry, similar security needs or goals.
Deliverable: a longlist of 6-10 strong options with brief notes on fit.

Step 7: Shortlist and pre-screen for expertise and industry fit
Narrow quickly. Pre-screen for must-haves: governance proven track record, your cloud stack, your compliance targets, and evidence of working with executive teams and boards. While evaluating candidates, watch for conflicts of interest (like being tied to a specific tool you don’t want).
Deliverable: a shortlist of 3-4 candidates with strengths, risks, and references to check.
Step 8: Conduct structured interviews and scenario-based evaluations
Run the same play with each finalist.
Use real-world scenarios:
- "A critical vulnerability is discovered in your main customer-facing application during a peak sales period. Walk through your decision process."
- "Your cloud infrastructure shows signs of potential data exfiltration. Describe your incident response approach."
- "The board requests a risk-adjusted security investment recommendation. Present your methodology."
Look for clarity, prioritization, and trade-off management. Ask for a short sample plan or one-page roadmap.
Deliverable: interview scorecards + side-by-side comparison.
Step 9: Validate references, credentials, and track record
Conduct reference interviews yourself. Speak with: a CEO about business alignment, a CTO about technical credibility, and a compliance lead about audit success. Verify claimed security improvements and incident response outcomes. Validate relevant certifications (CISSP, CISM, CCSP) and confirm technical competencies through specific examples.
Deliverable: reference notes + clear yes/no call.
Step 10: Complete legal and compliance due diligence
Close the risk loop before you sign. Execute NDAs. Run background checks where appropriate. Confirm data handling, privacy terms, and breach notification expectations. If you’re regulated or selling to regulated clients, align on processor obligations and cross-border data questions.
Deliverable: approved legal pack (NDA, MSA/SOW terms, data processing and confidentiality).
Step 11: Align on governance, communication, and reporting cadence
Decide how you’ll work together day to day. Who approves security policies and exceptions? How often do you meet with execs vs. working teams? What does the board want to see, and how often?
Standardize the dashboard: risk register, control coverage by domain, critical remediation aging, IR metrics, audit status, and top decisions needed.
Deliverable: a working cadence (weekly/biweekly/monthly), RACI, and a dashboard template.
Step 12: Finalize contract and onboard with a 90-day action plan
Sign the contract, then move fast. Kick off with stakeholder interviews, access provisioning, and a short discovery sprint.
Land a 90-day plan with 5-7 high-impact moves: close the top cyber risks, unblock deals, and hit audit milestones. End month one with visible wins and a clear runway for months two and three.
Deliverable: signed contract, access checklist, and 90-day plan with owners and dates.
How we help at TechMagic
Our experienced vCISO professionals start with a gap assessment, deliver a board-ready snapshot and detailed plan, then run the governance cadence with your team. You get clear priorities, measurable progress, and ongoing support during audits and security reviews without slowing down product work.
Well, now you know how to hire virtual CISO effectively and wisely. But let’s also see the common mistakes companies often make (with avoidance tips).

What Mistakes Should You Avoid When Hiring a vCISO?
These are the traps we see most often + simple ways to steer clear of them.
Mistake 1: Hiring without clear security goals or scope
When the “why” is fuzzy, the vCISO ends up spinning plates of ad-hoc tasks and tool shopping. Sales stalls on questionnaires, audits drift, and policy debt stacks up. A vCISO needs a clear North Star to prioritize trade-offs.
Impact: Misaligned priorities, wasted budget, and unresolved cybersecurity risks.
How to avoid it: Write a one-page brief that ties security to revenue, compliance challenges, and uptime. Name your top 3-5 outcomes and define which risks you’ll accept, mitigate, or avoid.
Mistake 2: Choosing based on cost instead of value and cybersecurity expertise
Chasing the lowest rate can backfire. Budget providers often under-scope governance, skip coaching, or drop off after handing you a “policy pack.” You save day one, then pay later in rework, delays, or failed audits.
Impact: Inexperienced hires may miss security risks that turn into multimillion-dollar breaches or fines.
How to avoid it: Judge proposals by outcomes and speed to impact. Ask for case studies and a 90-day cybersecurity plan. Not just a rate card.

Mistake 3: Overvaluing certifications, undervaluing leadership
Certifications demonstrate knowledge but not necessarily leadership effectiveness or technical depth. Strategic leadership requires translating technical risks to business impact, making difficult trade-off decisions, and maintaining team confidence during incidents.
Impact: Technically qualified but ineffective leaders who can’t sway executives.
How to avoid it: Test communication. Ask for a board-ready risk summary and a 10-minute roadmap pitch.
Mistake 4: Ignoring industry-specific experience
Every sector has landmines: healthcare data flows, fintech vendor chains, EU cross-border rules. A generalist may misapply controls or underestimate auditors, adding months to your timeline.
Impact: Failed audits, regulatory delays, and lost enterprise deals.
How to avoid it: Require proof of work in your sector and with target frameworks (ISO 27001, SOC 2, HIPAA, NIS2). Ask for artifacts, not just claims.
Mistake 5: Skipping KPIs and measurable outcomes
If you can’t measure it, you can’t defend the spend. Teams lose focus, boards see activity, not progress. KPIs keep everyone aligned and wins visible.
Impact: No ROI proof, no way to track maturity and security improvements.
How to avoid it: Lock a small KPI set: risk reduction, % control coverage, audit milestones, IR metrics, and sales-cycle impact.
Mistake 6: Overlooking cultural fit
A vCISO who “polices” instead of partnering will stall adoption. Engineering tunes out, compliance feels sidelined, and security becomes the blocker.
Impact: Poor collaboration, friction, and lack of trust.
How to avoid it: Include CIO/CTO/Head of IT in interviews. Run a cross-functional scenario and look for clarity, empathy, and pragmatism.
Mistake 7: Skipping background checks and references
Titles and logos can be misleading. vCISOs access your most sensitive security information: every vulnerability, incident, and weakness. Without checks, you won’t know if they can deliver at your scale.
Impact: Risk of overstated credentials or weak track record.
How to avoid it: Call references yourself (CEO, CTO, compliance lead). Confirm outcomes, timelines, and the candidate’s actual role. Verify relevant certifications only after fit is clear.
Mistake 8: Neglecting communication and reporting cadence
Great work still fails if execs can’t see it. Overly technical reports, irregular updates, or vague asks erode confidence and slow decisions.
Impact: Executives stay in the dark, board confidence drops, and remediation drags.
How to avoid it: Agree on governance up front: who decides what, meeting frequency, and update format.
At TechMagic, our vCISO cadence includes a monthly security committee, a living risk register, and quarterly board reporting. We keep everyone aligned without extra meetings. – Roman Kolodiy, Director of Cloud and Cybersecurity at TechMagic
Future of Cybersecurity Leadership: Why vCISO Is Here to Stay
Security leadership must evolve beyond traditional governance to address modern threats. Future security leaders must integrate technical expertise with business acumen while maintaining continuous security visibility. Organizations that establish proper vCISO engagement models with clear accountability and technical depth will achieve security resilience.
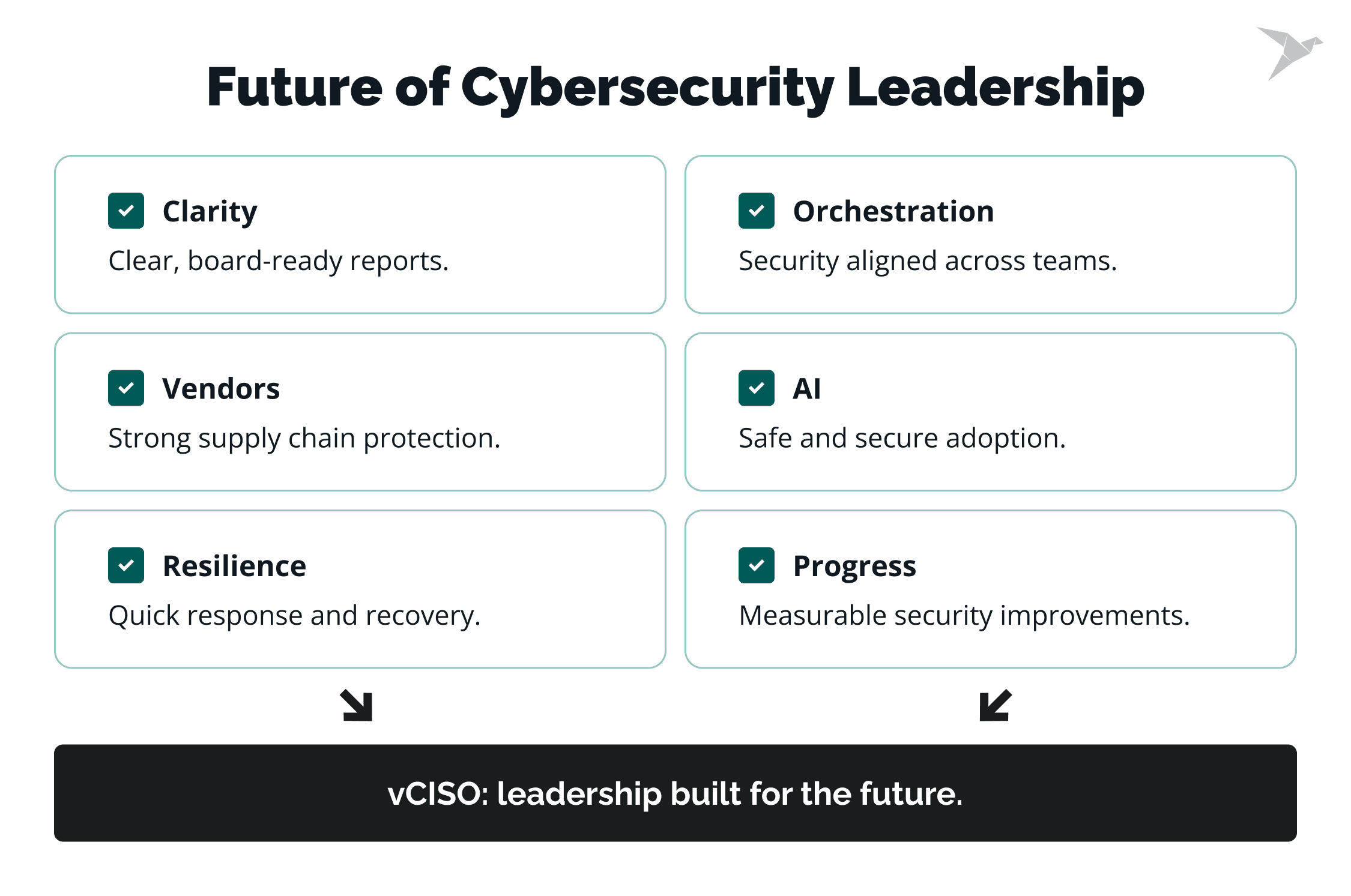
Here’s what will shape strong leadership in the years ahead and how a vCISO contributes.
Clarity for the board
Boards require risk quantification in financial terms: revenue impact, regulatory exposure, and recovery costs. With SEC, NIS2, and DORA mandating specific technical controls and rapid reporting, vague risk descriptions are insufficient.
vCISO's role: Ready-made reporting and board-friendly updates.
One plan across the business
Security can’t sit in silos. It needs orchestration across cloud, vendors, compliance, and product.
vCISO's role: Set direction and keep execution moving without the cost of a full-time hire.
Vendor and supply chain control
Supply chain attacks continue to increase in sophistication. Point-in-time assessments miss emerging risks. Organizations need continuous third-party security validation.
vCISO's role: Implement continuous vendor risk monitoring with automated scoring, regular validation, and clear remediation requirements.
Guardrails for AI and data
AI adoption introduces new attack surfaces and data risks. Organizations need governance frameworks that enable innovation while maintaining security.
vCISO's role: Establish adaptive security frameworks with clear risk assessment methodologies for emerging technologies.
Resilience over perfection
A perfect organization's cybersecurity posture isn’t real. What matters is how fast you respond, recover, and improve.
vCISO's role: Run scenarios, test playbooks, and track time-to-contain.
Visible progress
Stakeholders demand evidence of security improvement: reduced incident frequency, faster detection and response, improved third-party security, validated recovery capabilities.
vCISO's role: Comprehensive security metrics with continuous measurement and clear improvement trends.
Bottom line
The next era of leadership = clarity, orchestration, resilience, and results. Full-time CISOs are scarce and costly. Luckily, the vCISO model delivers senior leadership that scales with your stage.
Talk To Skilled TechMagic’s vCISO Team
Not ready for a full-time CISO but need real security leadership? We understand you.
The properly structured vCISO model provides senior security leadership that adapts to organizational needs while maintaining security effectiveness.
At TechMagic, our vCISO services incorporate these security best practices from day one. We establish clear governance structures, maintain continuous security visibility, and provide measurable security improvements.
We’ll tailor the engagement to your stage and priorities, so you get the right leadership, not extra overhead. If you need help steering strategy, getting through audits, or tightening vendor risk, we can step in quickly and make progress where it matters.
If you choose TechMagic's virtual CISO services, you’ll get:
- Clear direction that moves your company's cybersecurity program forward
- Hands-on compliance support and audit readiness
- Flexible, right-sized support that fits your team
If our virtual CISO services sound like the kind of help you need, let's talk! We’ll meet you where you are and move fast on what matters most.

Wrapping Up
Cybersecurity leadership isn't something you can put off. So it's time to understand how to find vCISO and take this step.
Relevant regulations get tougher, the threat landscape changes fast, and talent is hard to find. A vCISO offers a practical way to get the executive focus you need. Flexible, outcome-driven, and ready to deliver measurable progress without the wait for a permanent hire.
If you’re ready to explore this path, TechMagic's vCISO team can help you move quickly to your desired security initiatives and business objectives under strategic leadership.
FAQ

How much does it cost to hire a vCISO?
Most SMBs invest $5K-$15K/month for comprehensive security governance; larger or regulated firms may invest $20K+, depending on security requirements and incident response SLAs. Cost depends on scope, required availability, technical depth, frameworks, and security maturity requirements.
How is a vCISO different from a full-time CISO?
A vCISO gives you fractional executive leadership for strategy and governance, while a full-time CISO provides permanent ownership and day-to-day team management.
Can a vCISO help with SOC 2, ISO 27001, or HIPAA compliance?
Yes, experienced vCISOs can help ensure compliance and guide initiatives. vCISOs provide strategic guidance on compliance frameworks, help implement required technical controls, coordinate control validation, and manage audit preparation. They must integrate with your technical teams for control implementation and maintain continuous oversight.
What industries benefit most from hiring a vCISO?
Any business under industry standards or enterprise pressure (like SaaS, healthtech, fintech, e-commerce, professional services, or manufacturing) benefits from vCISO services. Such a security expert is especially effective for growth-stage companies establishing initial security governance and not ready for a full-time virtual chief information security officer, as well as organizations requiring specialized expertise for specific initiatives.

 Software Development
Software Development Security Services
Security Services Cloud Services
Cloud Services Other Services
Other Services















 TechMagic Academy
TechMagic Academy