How to Create an Incident Response Plan Your Security Team Will Actually Use
Last updated:9 December 2025
Most organizations don’t discover the weaknesses in their incident response plan until the moment an incident occurs. And by then, it’s too late. In fact, many IR plans fail not because teams lack skill, but because the plan doesn’t reflect how people actually work during high-pressure events.
This article breaks down what it really takes to build an incident response plan your team will trust and use. You’ll learn what a modern IR plan is, why so many fail in real-life scenarios, and how to create an incident response plan template, workflow-aligned playbook that supports fast decision-making when minutes matter.
We’ll also walk through the key elements every plan needs, how the NIST framework maps to daily operations, and how to involve your cybersecurity incident response team so the plan feels usable and aligns with expectations for handling security threats and future incidents.
Key takeaways
- Clear, practical guidance matters more than lengthy documentation.
- A modern IR plan must reflect real workflows, tools, and communication habits.
- Defined roles, incident categories, and simple playbooks speed up decision-making.
- Using the NIST framework helps teams structure effective cyber incident planning and response.
- Regular testing and updates keep the plan relevant as systems and cyber threats evolve.
- Involving analysts, engineers, and leadership early is essential for developing an incident response plan that people trust and follow.
What Is a Security Incident Response Plan?
A security incident response plan (IRP) is a documented, structured set of procedures for detecting, responding to, and recovering from cybersecurity incidents. It gives the cybersecurity incident response team a clear, repeatable workflow to follow when something goes wrong, including any security event that threatens sensitive data, business systems, or operations.
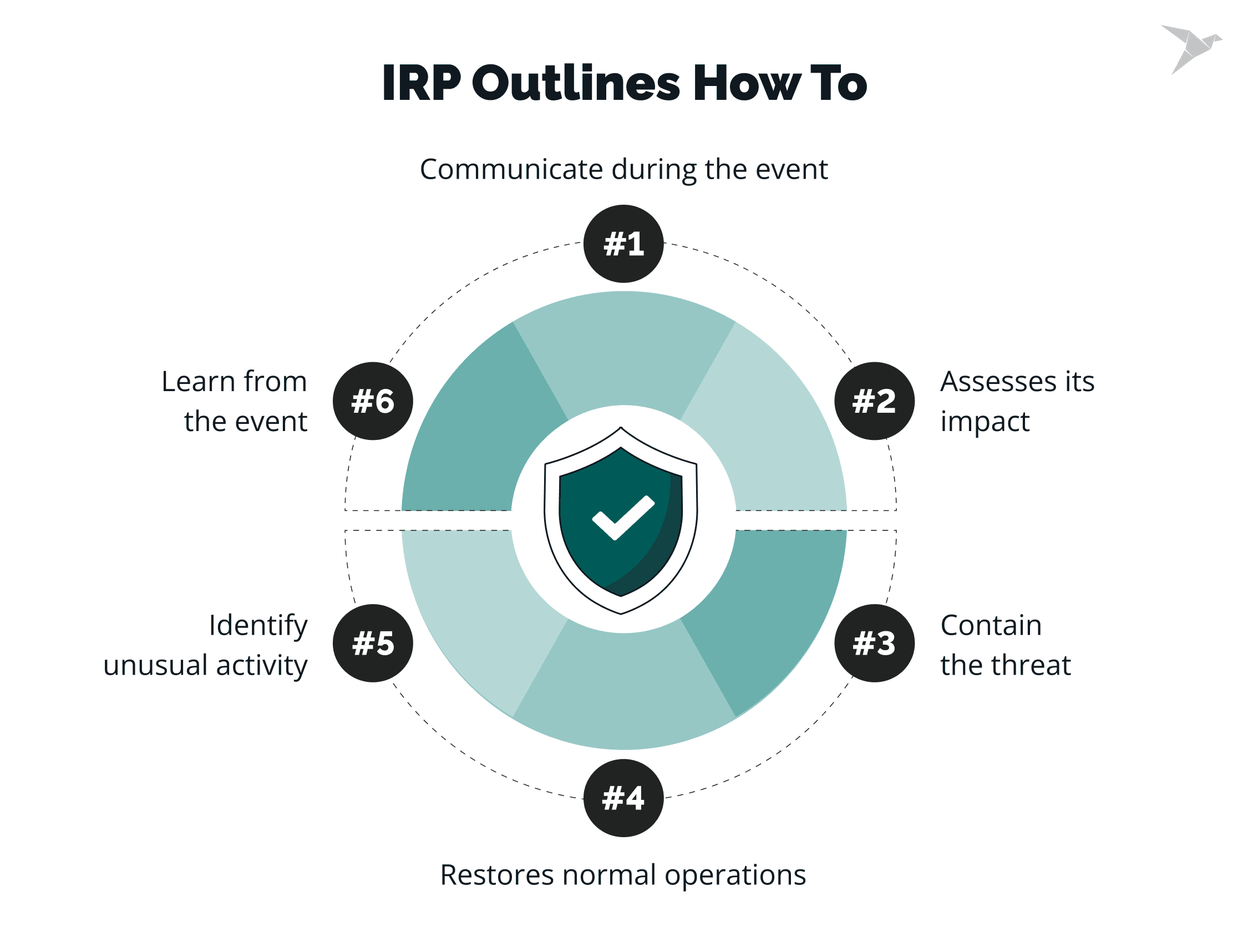
An effective IRP outlines how an organization:
- identifies unusual activity,
- assesses its impact,
- contains the threat,
- restores normal operations,
- learns from the event.
Its purpose goes beyond meeting compliance requirements. A well-built plan helps reduce damage, limit downtime, and control costs by ensuring the response is organized rather than reactive, especially during security breaches, data breaches, or situations that threaten crucial data.
Most IRPs include defined incident response roles, communication paths, technical steps, and incident response procedure guidelines. Together, these elements help the team act quickly, make informed decisions, and maintain operational continuity during stressful situations.
We are here to help

Why Do Many Incident Response Plans Fail in Real Life?
Many incident response plans fail because they don’t work the way teams actually operate during high-pressure incidents.
Let’s discuss this in more detail.
Too theoretical and generic
Some plans read like policy statements rather than practical guidance. They describe what should happen but not how to do it when the clock is ticking. During a security event, vague instructions slow the response and increase the risk of further damage.
For example, a plan might say “contain the threat immediately,” but offer no steps for isolating a compromised cloud workload or shutting down a misconfigured API. During an incident, vague instructions slow the incident response team down and create uncertainty.
Lack of clear roles and accountability
In many organizations, no one knows who has final authority during an incident. A common scenario: security analysts detect suspicious activity, but no one is sure who should approve taking a critical system offline. As a result, delays pile up, particularly concerning the affected systems, attackers maintain access, and the incident grows uncontrollably.
Without defined owners for decisions, incident response roles, escalation paths, and communication, even skilled incident response team members struggle to act with confidence.
Poor communication flow
Cybersecurity incident response planning often touches multiple groups: SOC, DevOps, legal, PR, leadership, vendors, and so on. If the plan doesn’t define how and when these groups communicate, information gets lost. Without a shared structure, response efforts can fragment and slow containment of security threats.
A real example: SOC analysts send updates in Slack, the IT team tracks actions in Jira, and leadership wants email summaries. The result is fragmented communication and an inconsistent understanding of incident status.
Outdated or unmaintained plans
Threats evolve fast. Infrastructure changes even faster. Many plans still reference systems that no longer exist or rely on contacts who left the company months ago. Plans that remain untested or outdated fail to protect sensitive data or guide teams through significant incidents.
When teams open the IRP during a crisis and see outdated tools, wrong phone numbers, or old architecture diagrams, they often abandon the document altogether.
No regular testing or simulations
Paper plans don’t survive first contact with a real attack and a security breach. Without tabletop exercises or live-fire simulations, teams never practice how they will collaborate. This leads to familiar breakdowns: missed steps, unclear priorities, duplicated work, and confusion about containment procedures.
Information overload
Some IRPs grow into massive binders full of dense text, complex flowcharts, and scenarios for every possible threat. In an emergency, no one has time to read a 70-page PDF. Overly complex plans slow response, increase stress, and cause teams to default to improvisation. They became nearly unusable during real security events.
These weaknesses reveal a simple truth: traditional incident response planning often fails because it’s built for documentation, not real-world use. Teams need a practical, streamlined approach that supports fast decision-making, clear communication, and predictable actions under pressure.
Penetration testing of a cloud-native hospital management system before the annual ISO 27001 audit
What Are the Core Elements of a Practical Incident Response Plan?
When you need to create an incident response plan, try to think of a clear structure that guides teams from detection to recovery with minimal confusion.
Below are the elements, including a communication plan, along with a strong business continuity plan and disaster recovery plan, that help responsible teams act quickly, coordinate effectively, and stay aligned during high-stress events.
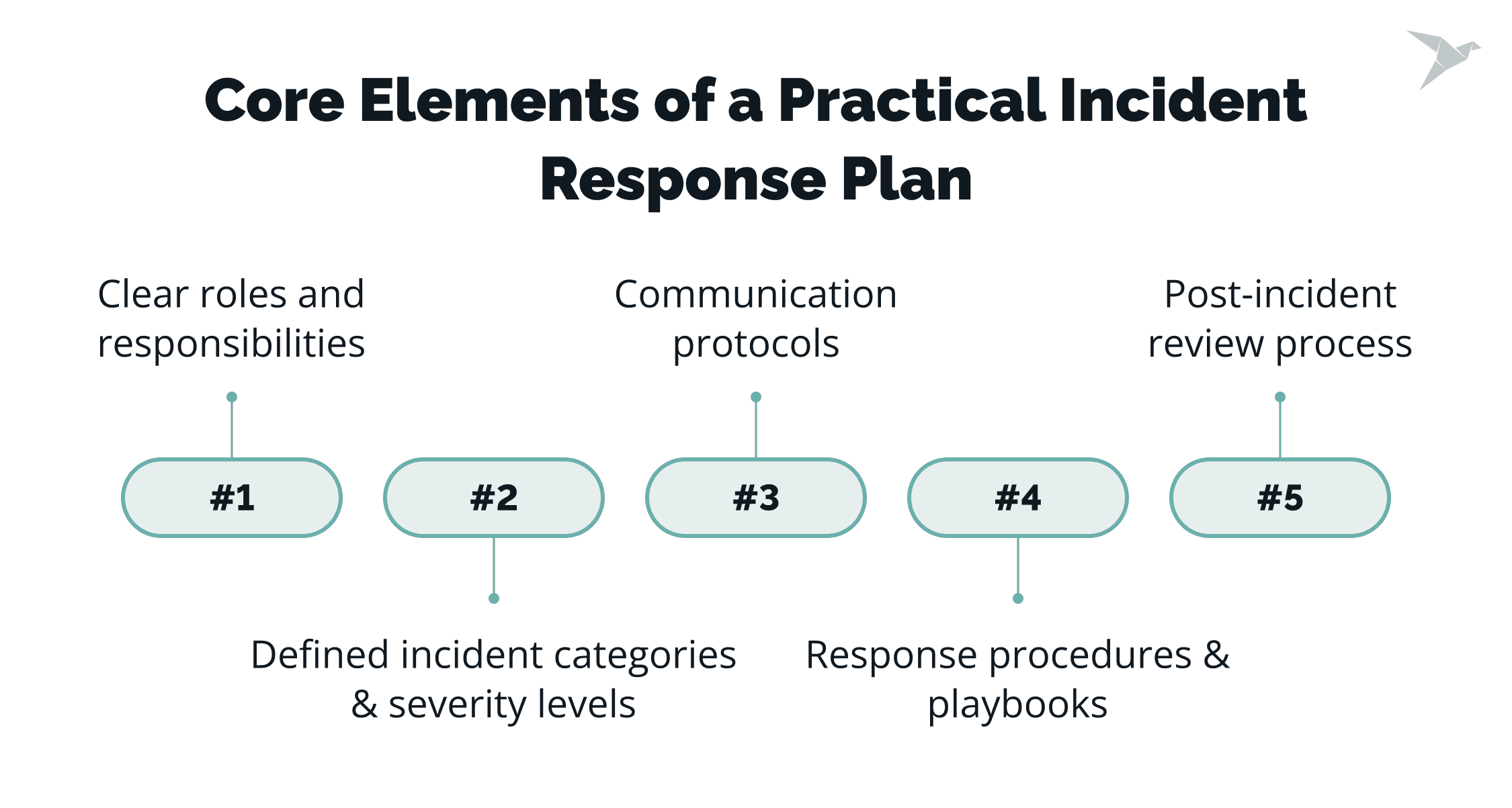
Clear roles and responsibilities
As we mentioned earlier, the chaos with roles and accountability makes IR plans ineffective. In contrast, a usable IRP clearly defines who does what during an incident.
This includes decision-makers, technical responders, communication leads, and escalation contacts. Clear ownership reduces, and defined incident handling roles prevent duplicated work and delays.
Defined incident categories and severity levels
Incidents vary in impact and urgency. The best advice on how to make an incident response plan is to classify them as low, medium, high, or critical. Your plan must explain what each level means.
It helps responders prioritize actions, allocate resources, and communicate the situation accurately to leadership. A clear structure also supports faster decisions during security breaches or any event threatening security data.
Response procedures and playbooks
Your incident response strategy should include a step-by-step guide for handling data breaches, unauthorized access, security threats, ransomware attacks, account compromise, DDoS attacks, or other scenarios. These become your core incident response steps. These playbooks describe the exact technical actions needed to contain and eradicate threats, making the response predictable and repeatable.
Communication protocols
Effective response depends on clear communication within the security team and across the organization. The plan should specify who needs to be informed, how often updates should be shared, and what channels to use. This ensures consistent, reliable communication from detection to resolution.
Effective communication is essential, especially when human resources, legal, PR, and engineering teams must coordinate.
Post-incident review process
A functional IR plan includes a structured way to learn from every incident. This process documents what happened, what worked, what didn’t, and what needs improvement.
Regular reviews help refine playbooks, update contact lists, strengthen the organization’s overall security posture, and reduce future incidents.
How to Build a Response Plan That Fits Your Team’s Real Workflow (Spoiler: NIST Framework)?
How to do an incident response plan that mirrors how your team already works? Align it with daily tools and communication habits. And, make sure it supports key compliance obligations, including GDPR’s 72-hour breach reporting rule, CCPA’s requirement to maintain an IR plan, and ISO 27001 controls for incident response.
The National Institute of Standards and Technology, or NIST Incident Response Framework, provides a cycle you can map directly to real workflows: Preparation, Detection and analysis, Containment, Eradication and recovery, and Post-incident activity. The steps below show how to build a plan that fits your environment while staying aligned with NIST and major regulations.
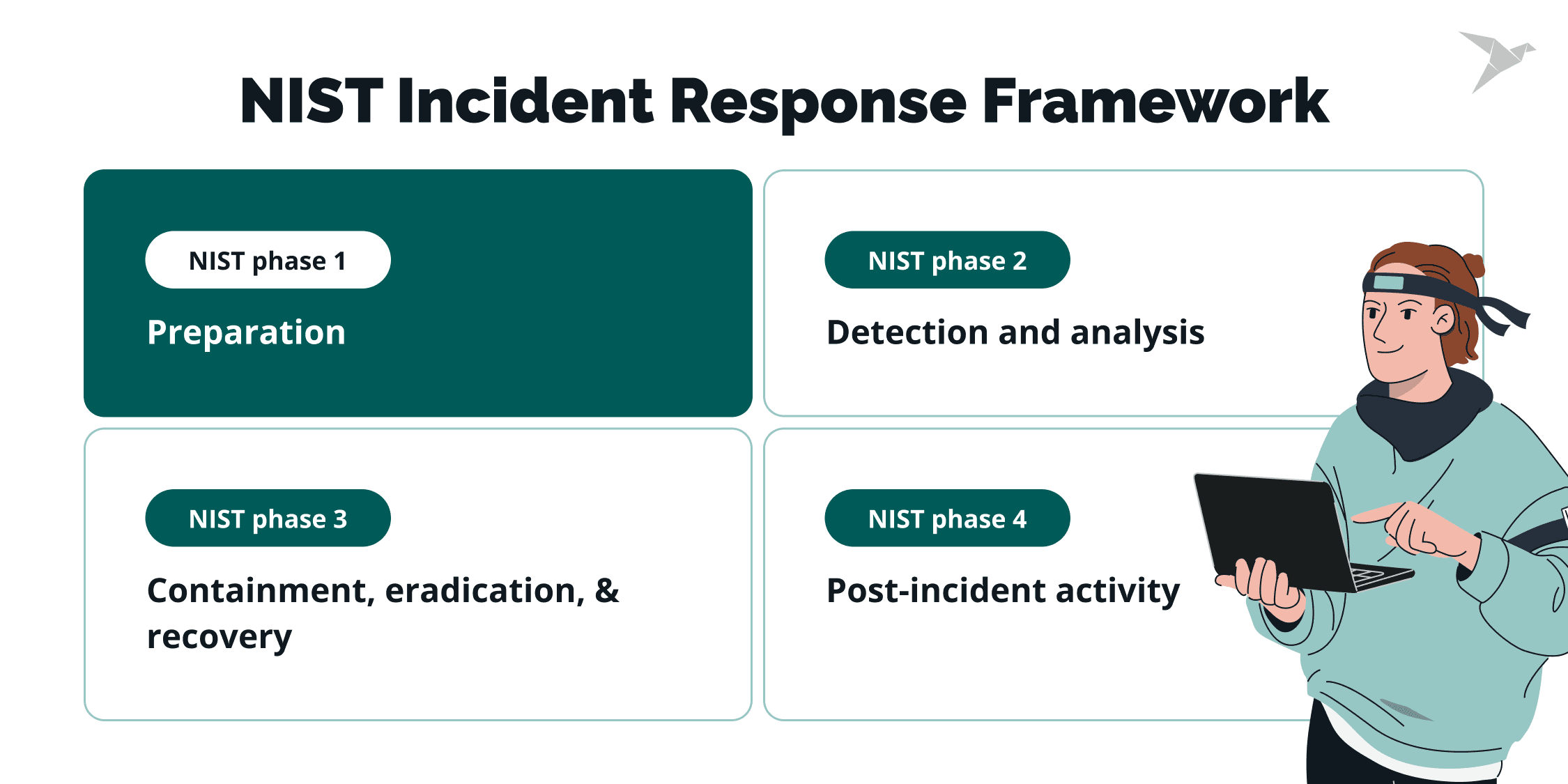
NIST phase 1: Preparation
In the incident response planning process, preparation covers the groundwork: roles, tools, workflows, and procedures. It is critical to choose proper security tools and verify that the attack surface is well understood.
Map how your team handles incidents today
Document what actually happens: who spots issues, where alerts appear, and how work is tracked. This reveals gaps that could slow you down during a real incident or delay compliance-driven reporting.
Identify your system of record and communication channels
Decide where incident work and updates will live, such as Jira or ServiceNow for tracking, SIEM or SOAR for monitoring, and Slack or Teams for collaboration. Your plan should live inside these tools, not in a disconnected document.
Define incident types, severity, and owners in the tools
Set clear responsibilities and classification levels directly in your systems. This supports ISO 27001 expectations for defined roles and helps demonstrate to auditors that you are handling breach risks responsibly. Score incidents based on their severity, identify lessons learned, efforts to restore systems, etc.
Turn playbooks into simple checklists and tasks
Convert procedures into short, clear checklists stored in your ticketing or knowledge tools. Lightweight guidance helps responders move quickly and reduces the chance of missing regulatory timelines such as GDPR’s 72-hour notification window.
NIST phase 2: Detection and analysis
This phase focuses on identifying incidents, assessing impact, and initiating the response as part of cybersecurity services. Strong threat detection improves speed and reduces further damage.
Integrate alerts with the plan
Configure your monitoring tools so high-severity alerts automatically create incident tickets and trigger predefined workflows. Automated tracking supports documentation needs for GDPR, CCPA, FTC, and internal audits.
Standardize communication during incidents
Define how updates are shared, where conversations happen, and what information is included. Consistent communication keeps teams aligned and ensures leadership, legal, and compliance teams receive accurate, timely information.
NIST phase 3: Containment, eradication, and recovery
Checklist-based steps help responders contain threats quickly and restore critical services as part of broader business continuity plan efforts. These actions rely on the structure and tools built earlier:
- Checklists guide isolation and remediation actions.
- Automated workflows help contain threats faster.
- Communication channels support coordinated recovery.
Alignment with NIST also reinforces ISO 27001 requirements for incident response and evidence handling.
NIST phase 4: Post-incident activity
This phase focuses on learning and improving. Teams refine playbooks, update tooling, and document improvements to reduce future incidents and strengthen overall security services.
Run tabletop exercises inside your actual tools
Test your plan using the systems you rely on:
- Walk through scenarios in SIEM, ticketing, Slack, PagerDuty.
- Identify delays and friction points.
- Adjust workflows based on what you find so that future attacks have less impact.
Exercises help ensure your team can meet strict reporting timelines like the GDPR 72-hour rule.
Review, refine, and keep the plan lightweight
After each incident, it's crucial to review the incident response lifecycle :
- Capture lessons learned.
- Update playbooks, tasks, routing rules.
- Remove outdated steps.
- Reflect any changes in GDPR, CCPA, ISO 27001, and FTC requirements.
Keeping the plan current supports audits and reduces the risk of penalties for late or incomplete breach reporting.
How to Involve Your Security Team in the Planning Process?
Your incident response plan is only effective if the people who use it trust it. A collaborative approach ensures the plan fits reality rather than assumptions. Engineers validate feasibility, SOC analysts test detection steps, and the management team confirms communication expectations.
- Ask analysts for practical input. They point out unclear steps and identify actions that don’t match real investigations.
- Check technical assumptions with engineers. They validate what is feasible and highlight system dependencies that the plan must consider.
- Get leadership alignment on expectations. This ensures priorities, communication rules, and reporting obligations are consistent.
- Review responsibilities as a group. Confirm who owns decisions, approvals, and communication so nothing is ambiguous.
- Run short working sessions to test clarity. Quick reviews help surface confusing or unrealistic areas before the plan is finalized.
- Keep a simple feedback loop open. Continuous input keeps the plan accurate as tools, teams, and environments change.
A collaborative incident response process builds shared ownership and results in a plan that the entire team can rely on under pressure.
CyberSecurity services for Elements.Cloud

Final Thoughts
A strong security incident response capability is a real competitive advantage. Organizations that treat it as a living, practiced capability respond faster, limit damage, protect critical services, and recover with greater confidence.
When you understand how to create an IR plan that matches real workflows, aligns with tools your team already uses, and reflects regulatory expectations, you give your security program a durable, repeatable way to handle pressure when it matters most. Clear roles, simple playbooks, defined communication paths, and regular testing all come together to create a plan your team will actually follow, even in the middle of a crisis.
Where IR planning is headed next
Incident response will continue to evolve as environments and threats change. Here are several trends to watch:
- More automation in detection and triage: Integrations with SIEM, SOAR, and EDR tools will reduce manual steps and speed up containment.
- Greater emphasis on regulatory readiness: Frameworks like GDPR, CCPA, and ISO 27001 will push teams toward more consistent documentation and faster reporting workflows.
- Continuous testing and simulation: Tabletop exercises inside real tools, not offline documents, will become the norm.
- Cross-team collaboration by design: an effective incident response plan will expand beyond SOC and engineering, giving legal, PR, and leadership clearer, more structured roles.
The future of incident response belongs to teams that build flexible, iterative processes. Expect more automation, clearer enterprise-wide coordination, deeper ties to risk management, and a stronger emphasis on aligning with industry best practices to reduce the impact of future attacks.
We’re here to support your next step toward a stronger, more resilient security posture

FAQ

What is an incident response plan, and why is it important?
A cyber security incident response plan is a structured set of procedures for detecting, managing, and recovering from incidents, including scenarios involving compromised systems or potential data loss. It helps reduce damage, limit downtime, support compliance, and ensure the security incident response team knows exactly what to do during high-pressure situations.
What are the key phases of an incident response plan?
Most frameworks, including NIST, follow these phases: Preparation, Detection and Analysis, Containment, Eradication and Recovery, and Post-Incident Activity. Together, they provide a repeatable cycle for handling incidents from start to finish.
NIST process support predictable steps from detection to recovery, including identifying the root cause and guiding next steps for affected parties.
How often should an IR plan be reviewed or updated?
Review the plan at least annually, or sooner if you experience a major incident, make significant infrastructure or organizational structure changes, or face new regulatory requirements. Regular updates keep responsibilities, workflows, and reporting expectations accurate. It is critical for senior management.
How can you test if your IR plan actually works?
You can test a formal incident response plan through tabletop exercises, simulated attacks, and tool-based walk-throughs. Realistic testing shows where the plan is unclear, whether the containment strategy is effective, where teams get blocked, and what needs to be refined – an essential part of learning how to create an IR security plan that performs under pressure.

 Software Development
Software Development Security Services
Security Services Cloud Services
Cloud Services Other Services
Other Services















 TechMagic Academy
TechMagic Academy











