Postman Security Testing


Ever wondered how to ensure the utmost security for your web applications and APIs? Or perhaps you've pondered how to navigate through the complex realm of cybersecurity vulnerabilities?
Enter Postman—an acclaimed API development environment that has transcended its original purpose to become an indispensable asset for security professionals and developers alike.
Originally heralded as an API development environment, Postman now stands as an indispensable asset for security experts and developers alike. Its inherent user-friendly interface and extensive feature suite extend far beyond the capabilities of conventional security scanners.
So, how does Postman achieve this? And you'd be right in asking how it differs from traditional security tools. Indeed, until recently, Postman's full potential might not have been fully realized. However, by harnessing its intuitive interface and robust features, security assessments reach new depths. In other words, Postman takes security scrutiny to the next level, going beyond what's expected from conventional tools.
Now, let's delve into how Postman functions as a robust security testing tool. Dissect its functionalities and explore its capabilities in identifying and addressing security vulnerabilities. But before we go any further, let's break down the key aspects that make Postman a formidable force in security testing.
6 Practical Use Cases of Postman for Security Testing
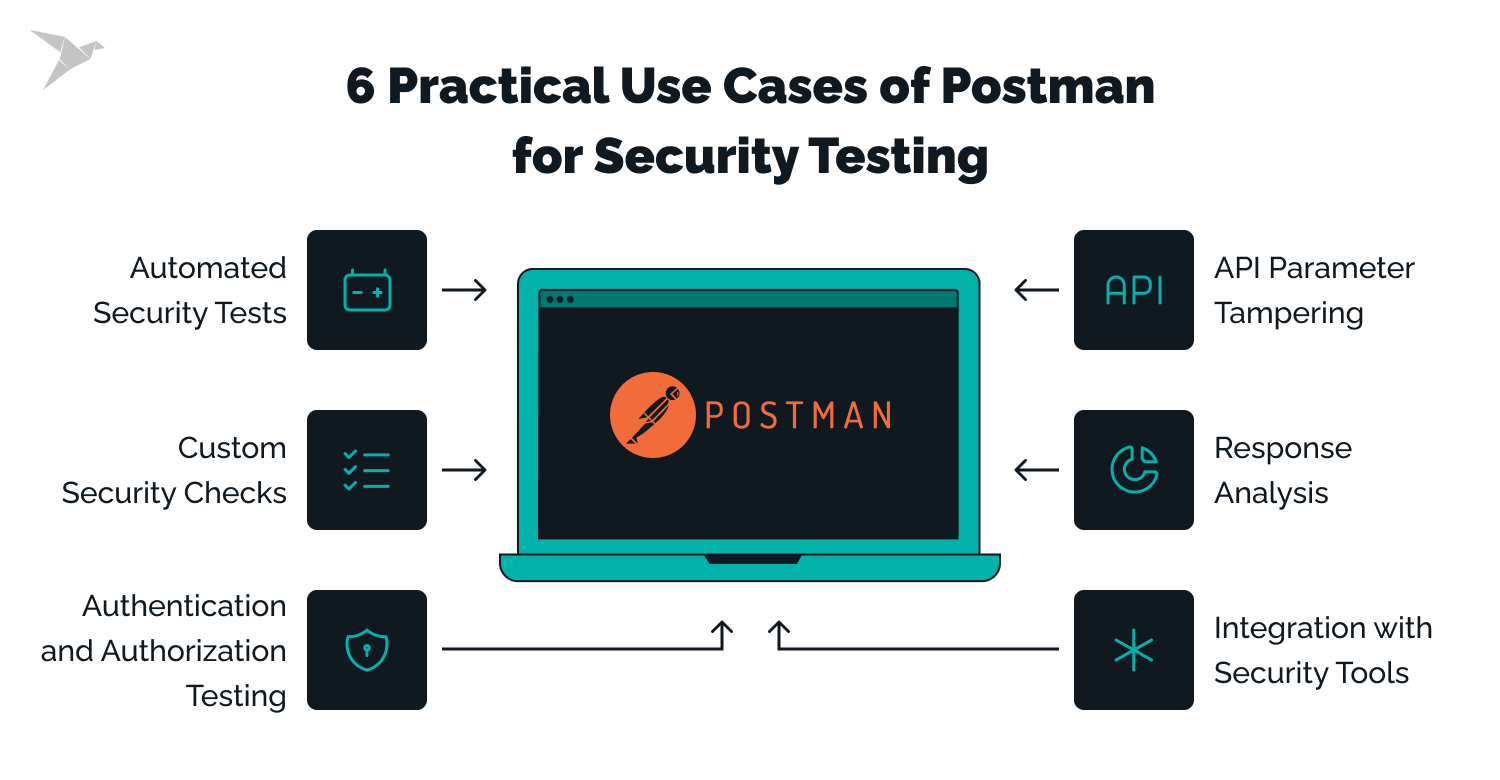
Here, we delve into six pivotal use cases that highlight how Postman redefines security testing. Explore these examples to unlock Postman's potential to fortify your digital assets against emerging threats.
Automated Security Tests
Ever wondered how effortless it can be to fortify your development pipeline with continuous security checks? Postman has the answer to automating security tests as part of the CI/CD pipeline. Imagine creating collections of API requests mimicking common attack scenarios like SQL injection or cross-site scripting (XSS). These collections act as vigilant gatekeepers, running tests seamlessly with each code change, effectively embedding security into your development rhythm
Custom Security Checks
But wait, there's more! Postman empowers you to craft customized security checks using JavaScript-based scripts. Picture delving deep into nuanced security assessments—scrutinizing token validity, dissecting session management, and uncovering elusive business logic flaws. These tailored checks offer invaluable insights that transcend the capabilities of automated tools.
Make sure building 100% secure app
Learn moreAuthentication and Authorization Testing
Let's explore the depth of your app's defenses. Postman enables seamless testing of authentication mechanisms such as OAuth 2.0 or JWT. Security teams simulate user roles and permissions, uncovering authorization loopholes and scrutinizing unauthorized access to API endpoints.
API Parameter Tampering
Now, imagine effortlessly tweaking API parameters for vulnerability testing. Postman allows swift modifications, making it a breeze to test how well your application handles user input validation and sanitization.
Response Analysis
Hold on! Postman isn't just about sending requests—it's about decoding responses too. Envision crafting scripts that meticulously analyze API responses, ferreting out sensitive data leaks, identifying excessive data exposure, or detecting unexpected response behaviors.
Integration with Security Tools
Here's the kicker! Postman seamlessly integrates with a plethora of security tools, expanding its horizons. Picture teaming up with OWASP ZAP for automated security scans or syncing with monitoring solutions for prompt result-based alerts. Postman's adaptability merges seamlessly with diverse security landscapes.
Ready to elevate your application security? These Postman use cases offer a roadmap for both security experts and developers. Let's delve into three practical use cases illuminating Postman's effectiveness in fortifying digital security.
But before that, let us hop in just for a second and offer you a free checklist that simplifies a choice of security vendor in case you'll want to outsource that:
Postman Testing for SQL Injection Vulnerabilities
Let's get started by exploring the first test case, focusing on SQL Injection. Our aim is to scrutinize the Juice Shop's search or query functionalities for potential SQL injection vulnerabilities.
In this instance, we'll craft a Postman request directed at the login endpoint, embedding malicious SQL payloads. This test assesses whether the application responds with database errors or presents unexpected data.
Step 1. Request Setup:
- Let's begin by creating a Postman request that mimics a database query—such as product searches or login submissions.
- Method: Set the request method as POST.
- Endpoint: Specify the search endpoint URL (e.g., /rest/user/login).
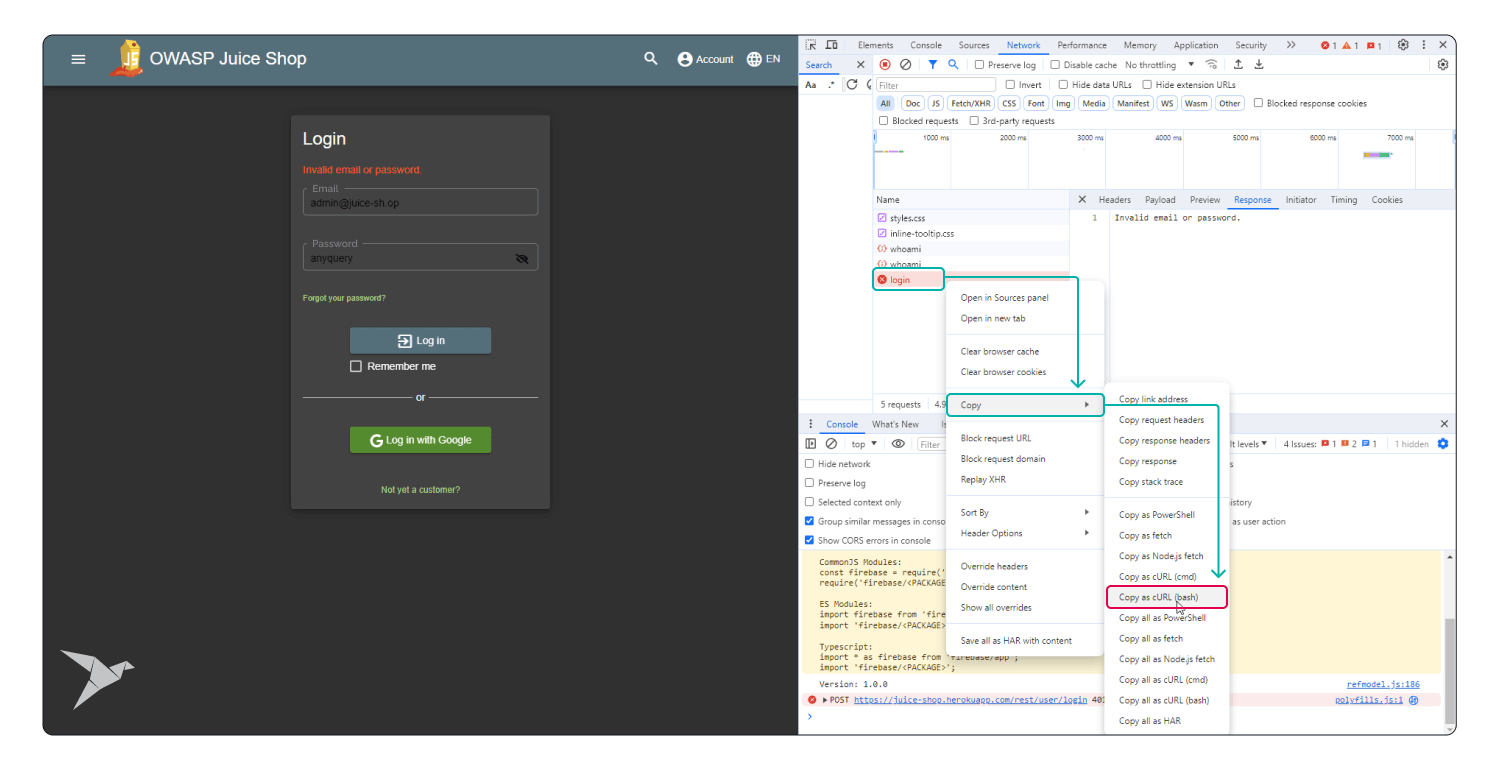
Step 2. Payload Injection:
- In the URL query parameter, we'll insert a malicious SQL payload, for example, '--;
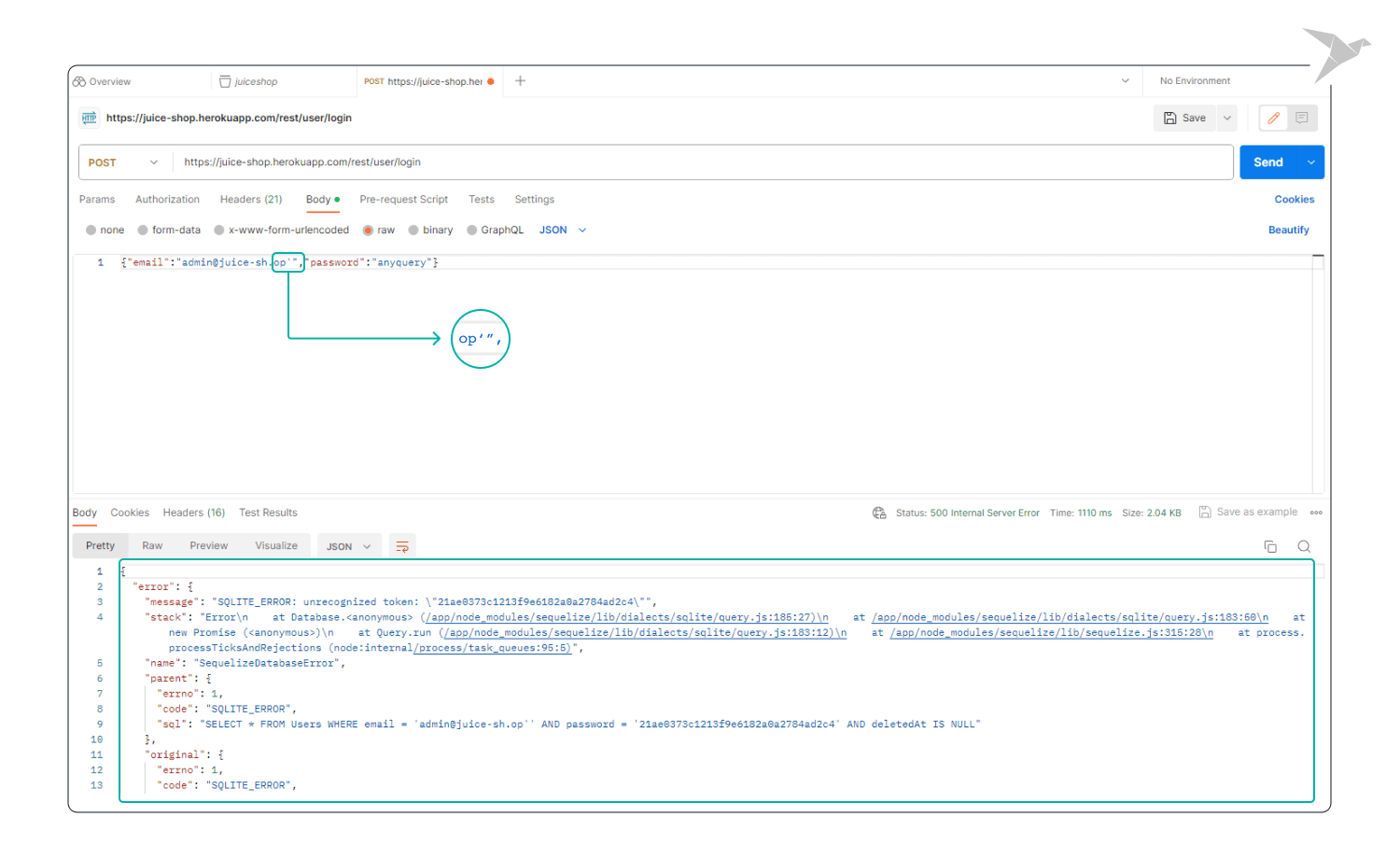
Step 3. Test Execution:
- Send the request and carefully observe the application's response.
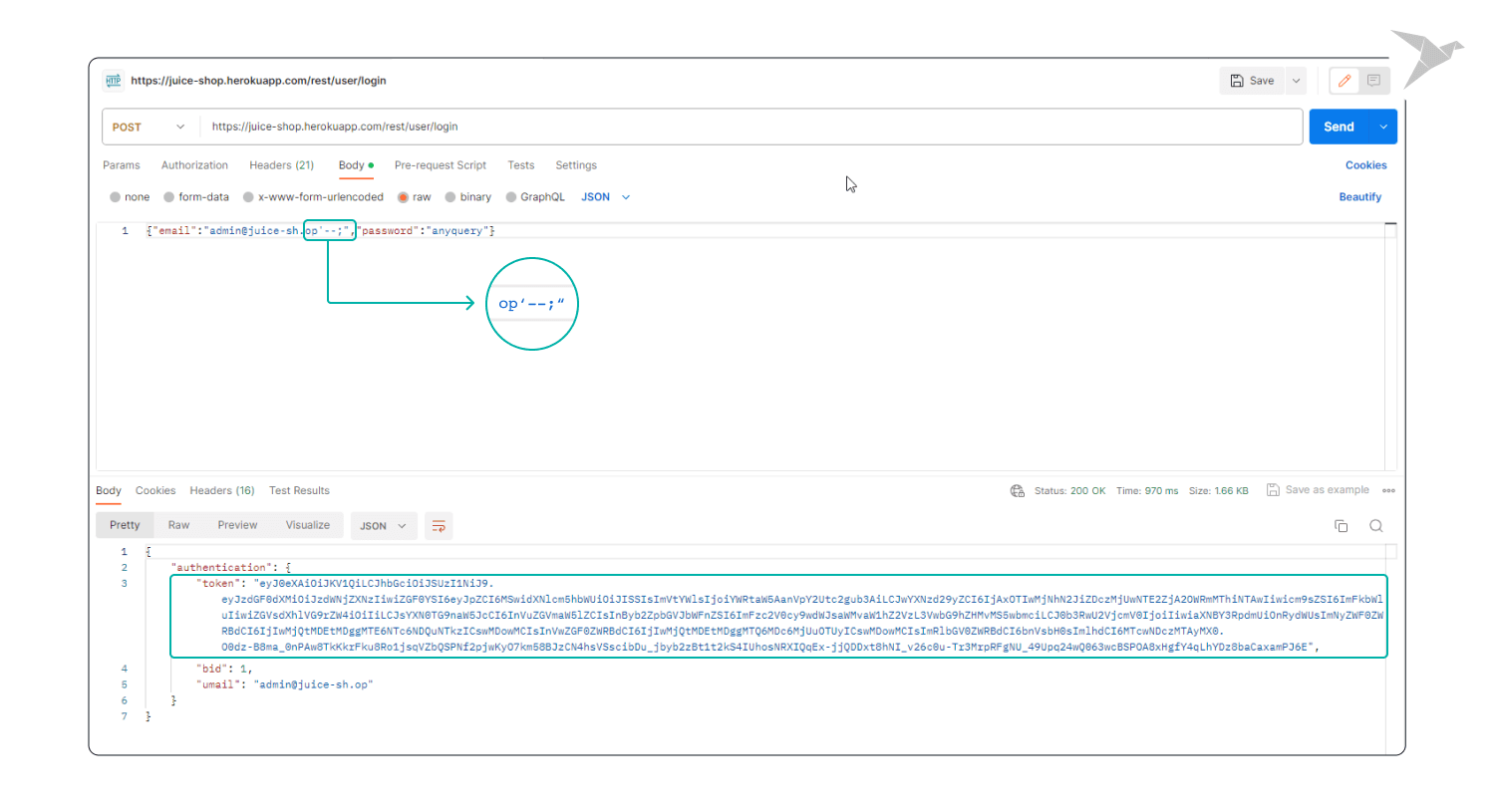
Outcome: If you encounter error messages highlighting SQL syntax issues, it could signal a potential SQL Injection vulnerability. Also, if you receive unexpected results or error messages, it may indicate an SQL injection vulnerability.
Additionally, let's conduct some tests within the TEST tab to further evaluate the response. These tests will scrutinize the response for indications of vulnerability to SQL injection. Depending on the response content, we'll assess if the API is vulnerable and potentially exposes hidden data.
> let text = 'Your api is safe from SQL injection vulnerability'
pm.test("checks response for WHERE clause sql injection", function() {
if(pm.response.text().toLowerCase().includes("error")){
text = "Maybe your API is vulnerable to SQL injection vulnerability which allows the retrieval of hidden data"
}
pm.expect(pm.response.text().toLowerCase()).to.not.include("error")
});
let template = `
<div style="align-items:center;display:flex;justify-content:center;margin-top:16px">
<div style="padding:16px; font-family:Inter, OpenSans, Helvetica, Arial, sans-serif; border:1px solid #ccc; text-align:center; vertical-align:middle; border-radius:8px;background-color:#f2f2f2">
<span >{{text}}</span/>
<br/>
<span>Learn more at <u>{{link}}</u></span>
</div>
</div>
`;
pm.visualizer.set(template,{
text:text,
link:"https://portswigger.net/web-security/sql-injection"
});
Let's ensure your API remains resilient against SQL injection vulnerabilities.
Postman Testing for Cross-Site Scripting (XSS) vulnerabilities
Let's move on to the second test case, focusing on Cross-Site Scripting (XSS).
Our objective is to scrutinize Juice Shop for potential XSS vulnerabilities. Imagine creating a Postman request to submit user-generated content, such as a product review or a chat message, embedding a malicious script payload. Our aim is to observe how the application responds when faced with this injected script payload.
Step 1. Request Setup:
- Let's simulate a user input scenario by crafting a Postman request—such as submitting a product review or a chat message.
- Method: Set the request method as POST.
- Endpoint: Specify the relevant endpoint URL (e.g., /api/Feedbacks).
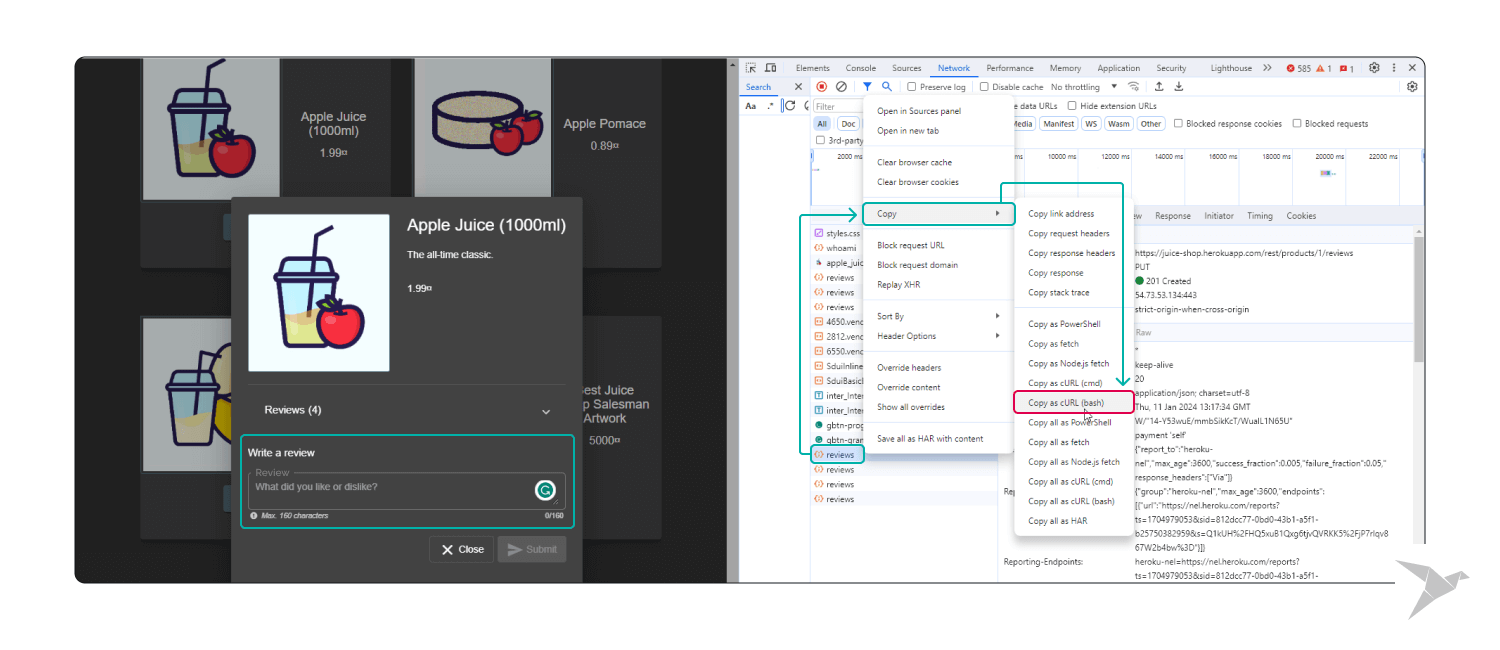
Step 2. Payload Injection:
- Inject a malicious script payload into the request body as part of the input data.
- For instance, set the comment text to <script>alert('XSS')</script>.
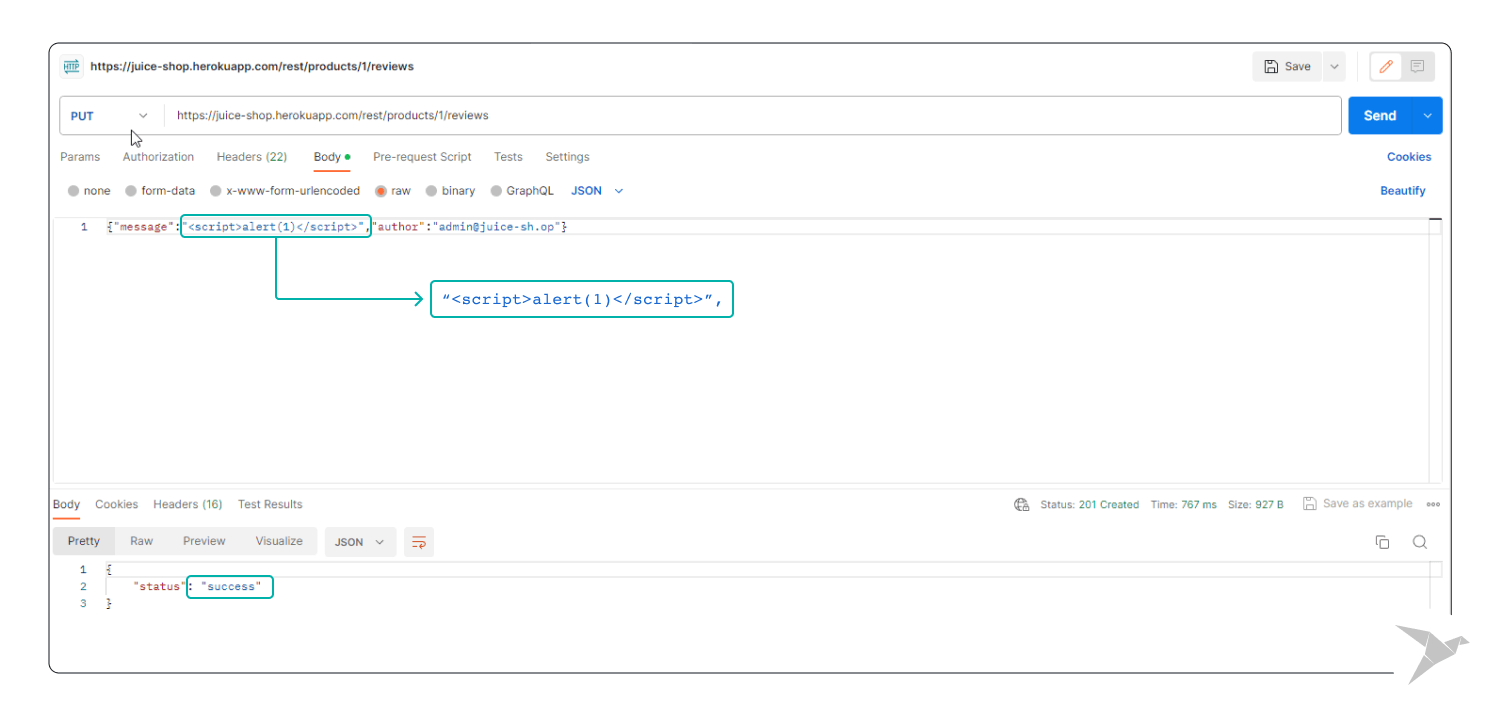
Step 3. Test Execution:
- Send the request and closely observe the application's response.
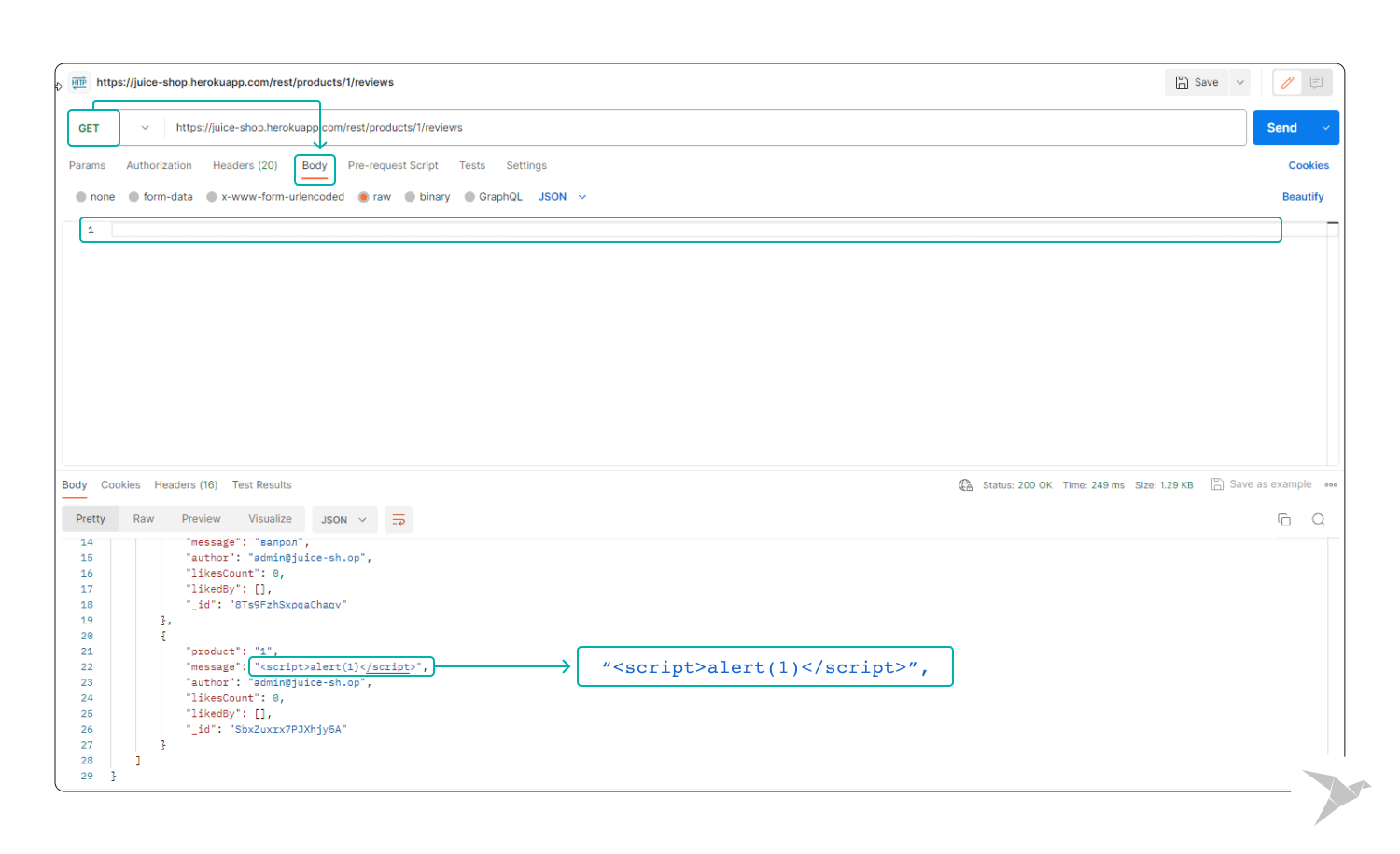
Outcome: If an alert popup appears, it might indicate a potential XSS vulnerability in the application. Or if the application doesn't properly sanitize and escape user input, the injected script may execute, indicating a potential vulnerability to XSS attacks.
Postman Testing for Broken Access Control Issues
Let's move ahead with the third test case, focusing on identifying Broken Access Control vulnerabilities.
Our goal is to pinpoint potential Broken Access Control vulnerabilities in the Juice Shop application. Imagine creating a Postman request that simulates an access control scenario—like placing an order—and scrutinizes how the application responds:
Step 1. Request Setup:
- Craft a Postman request that replicates an access control scenario, such as placing an order.
- Method: Set the request method to POST.
- Endpoint: Specify the order placement endpoint URL (e.g., /api/BasketItems).
Step 2. Manipulate Business Logic:
- In the request body, attempt to manipulate request parameters or payload in a manner that impacts access control.
- For instance, try placing an order using another user's basket ID.
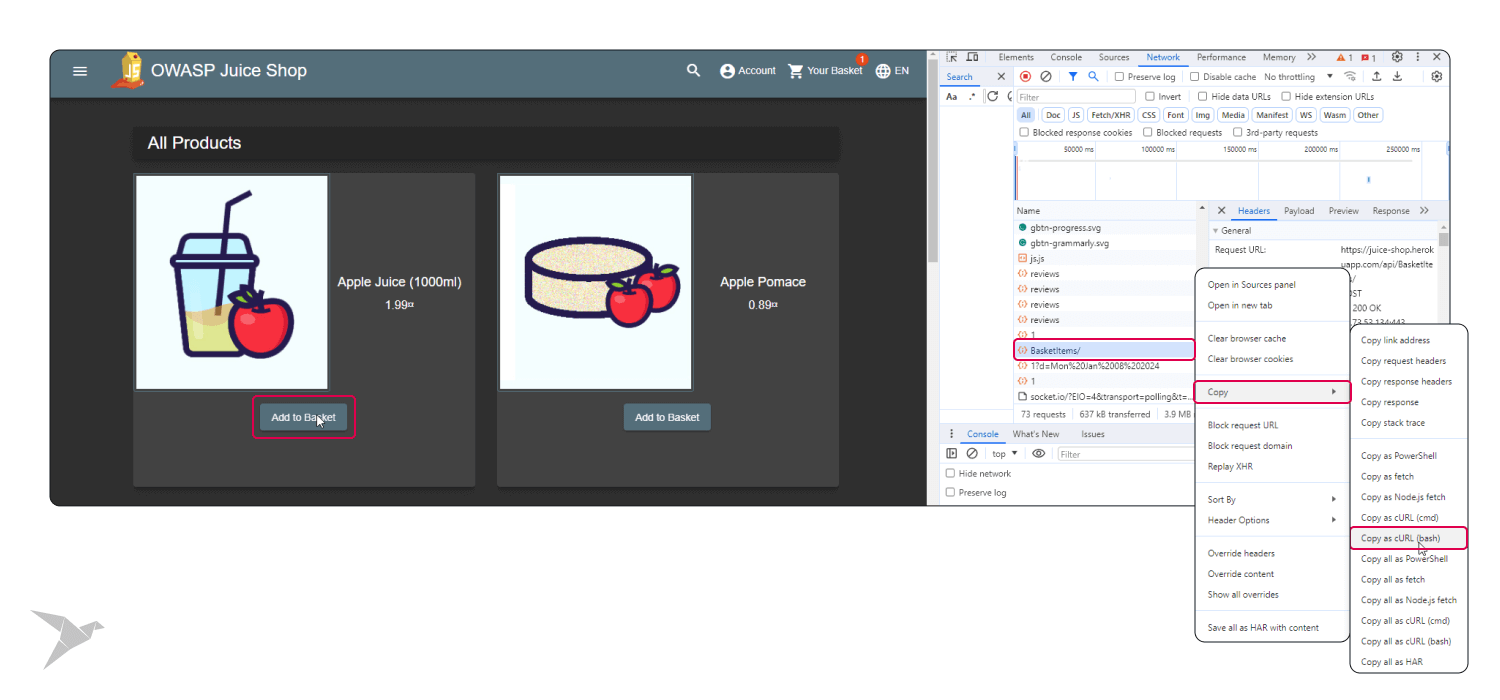
Step 3. Test Execution:
- Send the request and carefully observe the application's handling of the request. If the application allows modifications to another user's basket, it may signify a potential Broken Access Control issue.
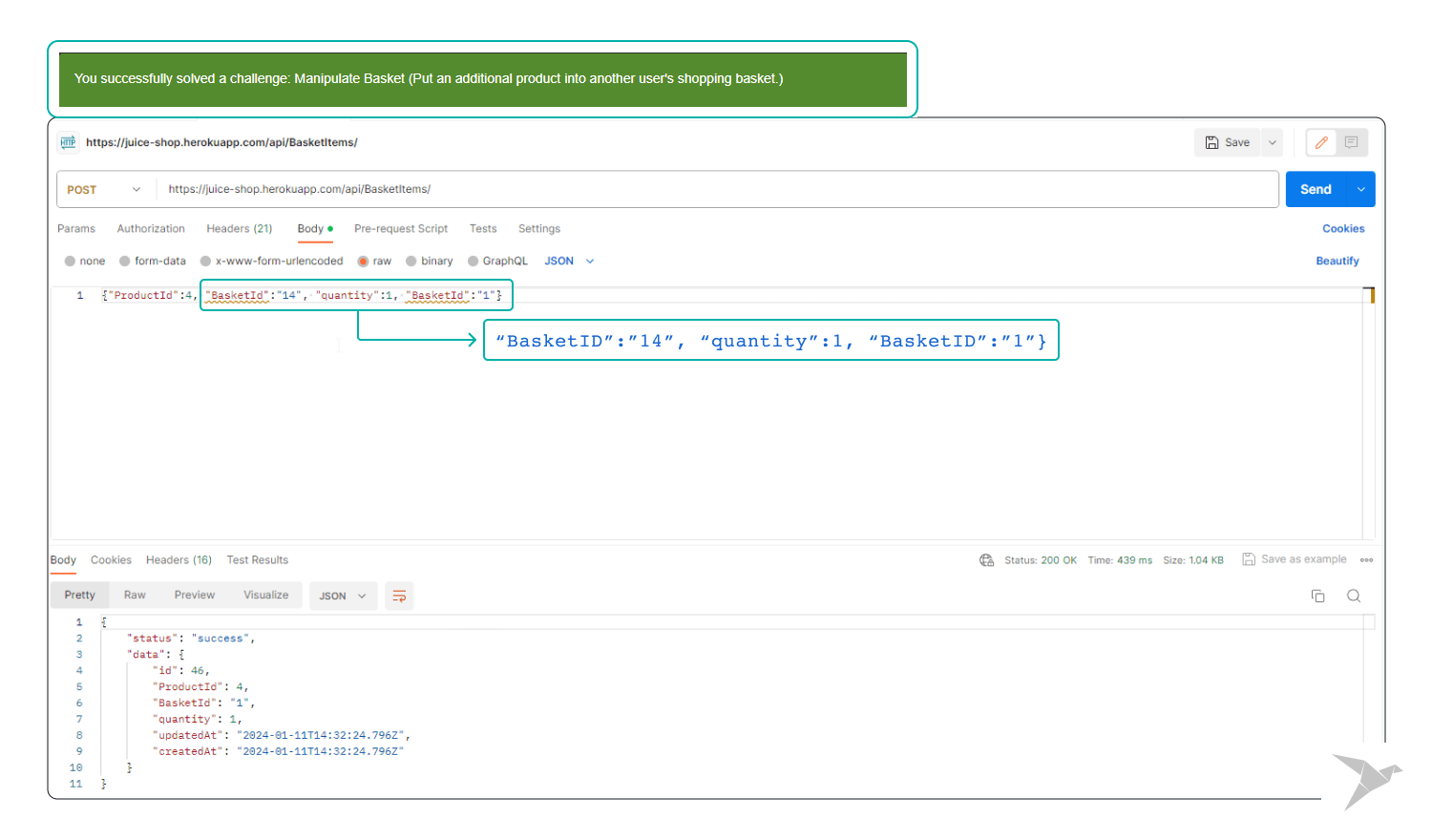
Identify instances where the application fails to enforce proper access control, potentially enabling manipulation of others' data. For instance, the predictability of basket IDs might allow adding products to other users' baskets, highlighting a potential vulnerability.
Outcome: This test aims to identify instances where the application exhibits signs of Broken Access Control, allowing unauthorized access to manipulate or access other users' data. Specifically, scenarios where the system fails to enforce strict access controls, thereby permitting users to tamper with or view data that should be restricted, will be highlighted. This vulnerability could lead to unauthorized data modifications or access, compromising the application's security and integrity.
Wrapping Up
Postman is a robust tool, celebrated for its API testing and development capabilities. It offers a rich spectrum of features crucial for thorough security testing, empowering professionals to fortify web application security. Let's dive into how Postman excels in this domain:
- Efficient API Testing
- Collection and Environment Management
- Pre-Request Scripts
- Data-Driven Testing
- Customizable Scripts
- Security Automation Integration
- Collaboration and Reporting
- Documentation and Training
Postman's adaptability, automation prowess, and user-friendly interface make it a linchpin for security testing endeavors. It is pivotal in scrutinizing APIs, simulating attacks, and conducting comprehensive assessments. Embracing Postman responsibly and ethically, ensuring proper authorization and adherence to security best practices, is essential when conducting security assessments.
Harnessing its power within ethical boundaries is key to fortifying application security and fostering a safer digital landscape.
Ensure your product security and data protection
Learn more



 linkedin
linkedin
 facebook
facebook
 twitter
twitter






















